Powerful Phishing and Ransomware Protection
Stop Social Engineering and CEO Fraud
Stay One Step Ahead of the Attackers
The Retarus Advantage
Cutting-Edge Technology
European Data Protection
Transparency Builds Trust
Customer Ratings and Reviews
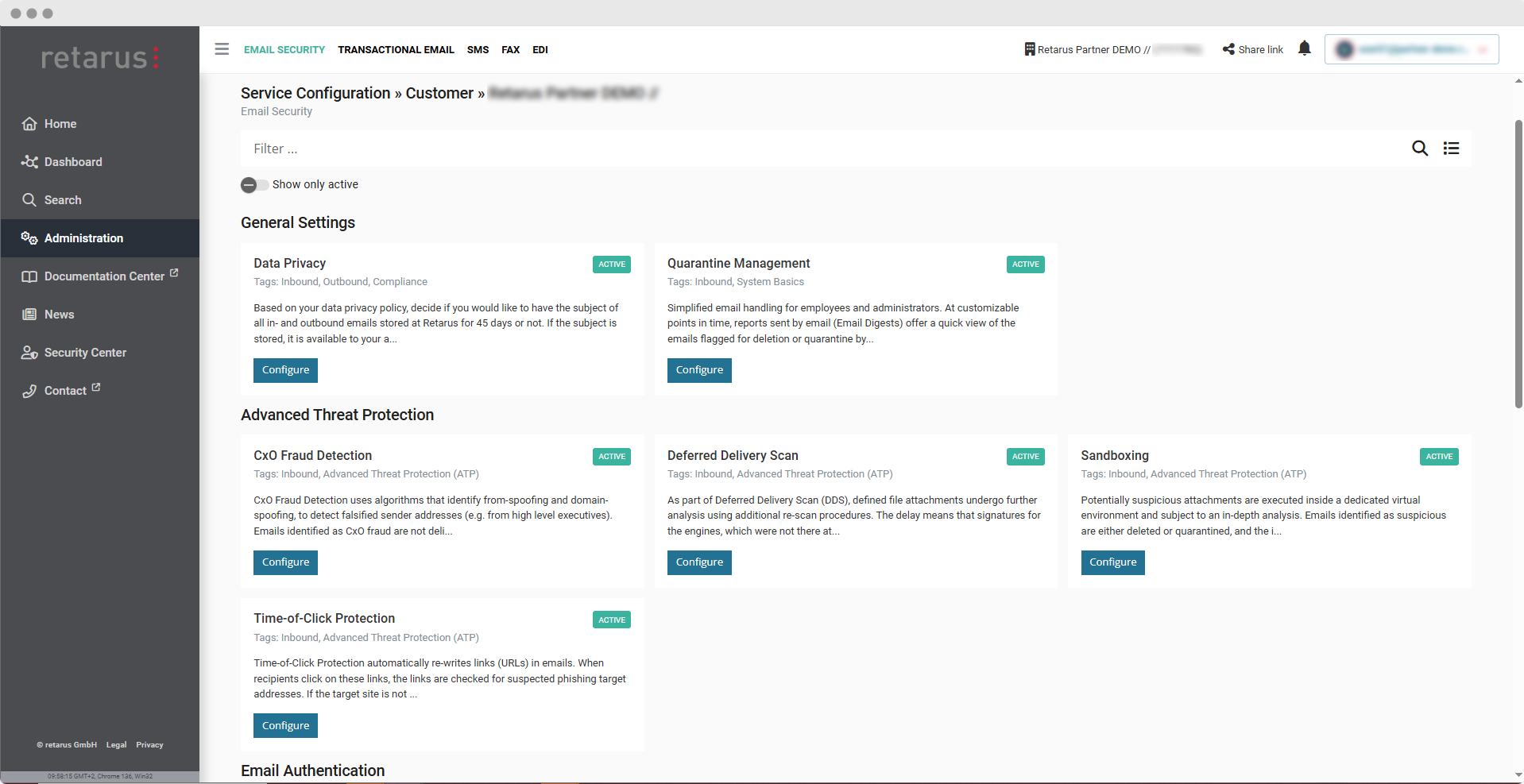
Features
- Analyzes MIME type, actual content, and hash values
- Extracts text and fingerprints attachments (e.g., HTML, PDF, DOC)
- Extracts URLs from attachments to assess potential risk
- Unzips and scans ZIP files
- Detect phishing in PDF and HTML forms
- Analyzes images to block image-only spam (e.g., QR codes)
- Classifies similar images using color histograms, plus OCR, face, and logo recognition to identify scam campaigns
- Analyzes header details
- Checks for domains and character sets which are similar in appearance (domain similarity)
- Detects forged sender names, “from” spoofing or “domain” spoofing.
- Delivers legitimate emails via email authentication (SPF) and allowlists
Why Choose Retarus’ Email Security and Management Solutions?
All-Encompassing, Flexible Cloud Offering
Local Processing Guaranteed
30+ Years of Enterprise Project Experience
Real Experts, In-House Support
What's Next?
Frequently Asked Questions
Which data does Retarus require for the analysis and how is it used?
We only extract selected metadata, such as file properties or hash values, and check these details against threat intelligence databases. As a rule, this data is anonymized and allows no conclusions to be drawn about content or persons.
How does Retarus ATP differ from conventional email security solutions?
The large number of data sources sets us apart. We employ a multi-layered approach to protection, with proactive detection methods such as heuristic analysis, multi-scanning and behavior analysis. This enables our ATP to detect even novel or specially developed malware reliably – before conventional solutions have a chance to react.
Is Retarus ATP also suitable for hybrid or cloud environments?
Yes, our solution is designed to integrate flexibly into existing on-prem, cloud or hybrid infrastructures. We offer connection via MX record (secure email gateway) or connector (ICES approach).
What role does AI play in the Retarus ATP protection strategy?
Our AI-powered filters are always used in a supplementary role. They provide especially valuable support in recognizing complex phishing attacks and analyzing contents, sender behavior and context details.
How does Retarus ATP support our IT department in its daily work?
With neatly designed dashboards, automated reports and granular guidelines, the solution reduces your IT team’s admin workload and helpdesk requests through effortless user self-service (online quarantine and daily email digests).
Which information do admins receive regarding threats?
For each step concluded in its checks, Retarus provides a tracking point with the respective outcome. Presented in a tidy overview within the admin portal, these points enable gapless insight into the reasons an email has been blocked, delivered or placed in quarantine – ideal for audits, traceability and quick error analysis. In addition, we provide a wide range of events to feed into your existing SIEM tool via an interface.