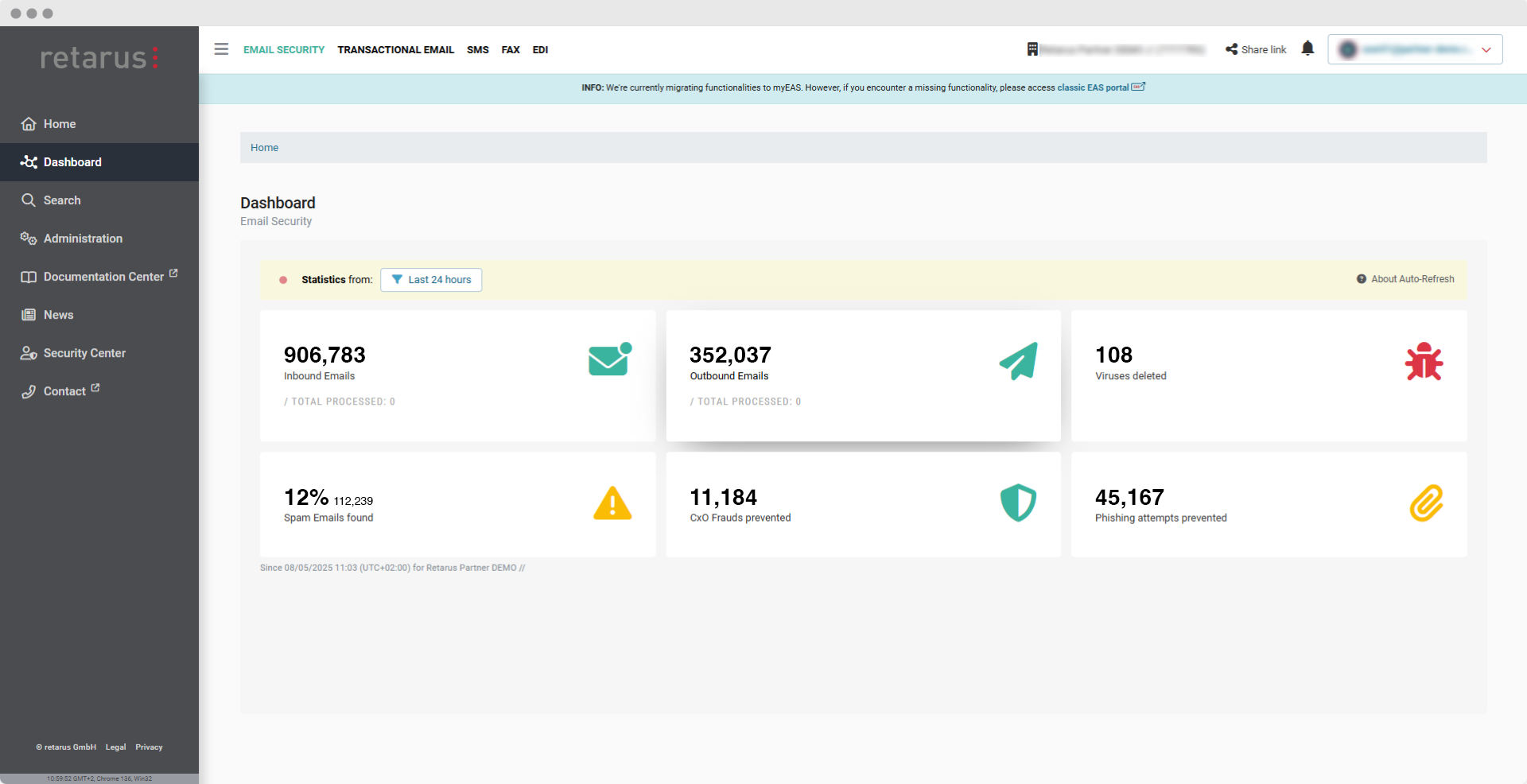
Effective, Multi-Faceted Protection
Uncompromising Security, Minimal Effort
MS 365 Connection Preferred?
Explore our ICES deployment model, with connectors for Microsoft 365 and more.
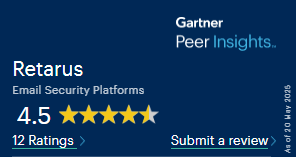
Customer Ratings and Reviews
Explore Our Security Portfolio
Retarus Is a Radicati “Top Player”
Discover why leading analysts consistently rank Retarus among the top email security providers.
News, Trends and Insights
Keep up to date on important product and sector developments with our corporate blog.
Product Info at a Glance
Find data sheets, manuals, and more in our Product Documentation Center.
Our Experience, Your Advantage
Discover how we help companies around the globe to secure their email communication effectively.
Frequently Asked Questions
How is the Retarus Secure Email Gateway implemented?
Implementing the Secure Email Gateway is incredibly simple: Just a quick MX record change is all it takes – no need to adapt your existing infrastructure. This is ideal for uniform, hybrid, or distributed IT environments. For pure Microsoft 365 setups, an ICES deployment model is also available.
Can I also integrate my existing SIEM tools or other security components?
Yes, absolutely. We transmit diverse event types to well-known SIEM systems via standardized interfaces. Our experts also have extensive project experience in seamlessly integrating other third-party security components our customers might use, like encryption or sandboxing solutions.
How is post-delivery protection achieved?
Our Europe-patented Retarus Patient Zero Detection identifies potentially dangerous emails even after delivery, triggering warnings and enabling an automated clawback function. Additionally, our Time-of-Click Protection analyzes all links in real-time using URL rewriting.
How can my users interact with the email security service?
Retarus provides a user-friendly online quarantine portal with daily email digests in 11 languages. Users can view and release quarantined emails, in addition to managing their personal block and allow lists. This significantly reduces the volume of helpdesk tickets and improves user awareness.
Is the solution GDPR compliant?
Absolutely. Retarus always processes all data exclusively in self-operated data centers, consciously opting against hyperscalers. Local processing is contractually guaranteed. We provide tamper-proof logs, compliance documentation and actively support customer-specific audits – especially crucial for regulated sectors. Headquartered in Germany and with no external investors, we offer our customers maximum data sovereignty – reliably, even in politically challenging times. Learn more on this topic here.