The standards you need
Transparent costs
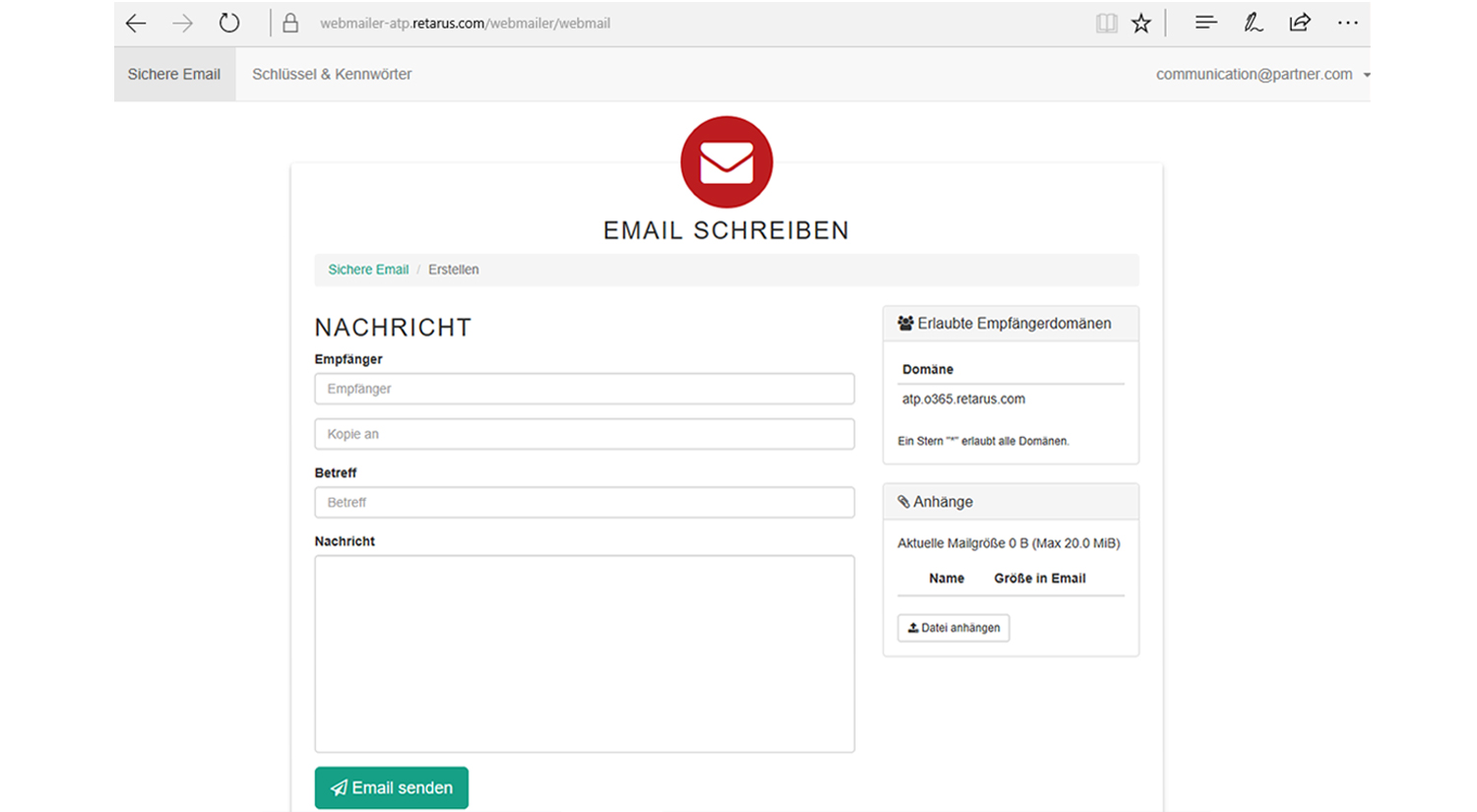
Secure webmail service
The Retarus Advantage
Effortless Integration
Key Management Made Easy
Simple Synchronization
Customer Ratings and Reviews
Features
Retarus Email Security: The European Advantage
Full-Service Cloud Offering
Truly European, No Compromises
Enterprise Expertise Since 1992
Real People, Real Support
What's Next?
Learn more about Retarus Email Security!
On-demand Webinar About Encryption
Discover how to make encrypted communication easy for everyone (Webinar in German)
Product Details, Manuals and More
Find data sheets, manuals, and technical specs in our Product Documentation Center
News, Trends and Insights
Stay informed on industry trends and product developments via our corporate blog
Frequently Asked Questions
What about the “last mile”?
To secure your connection with Retarus, you can choose between TLS or a VPN.
Which email systems is Retarus Email Encryption compatible with?
Our encryption solution works with all SMTP-based email systems, including Microsoft 365, Google Workspace, Microsoft Exchange, and HCL Notes Domino.
Can I use Retarus Email Encryption and Retarus Email Archive in combination?
Yes – and it's especially beneficial. When used together, encrypted emails are automatically decrypted upon receipt and then re-encrypted using the archive master key. This ensures compliant archiving and long-term readability – even if employees leave or keys are no longer available.
Where can I find more information about the solution?
Check out our customer stories, analyst reports and corporate blog. Stay informed about upcoming events and webinars – or book a demo. We are happy to help.