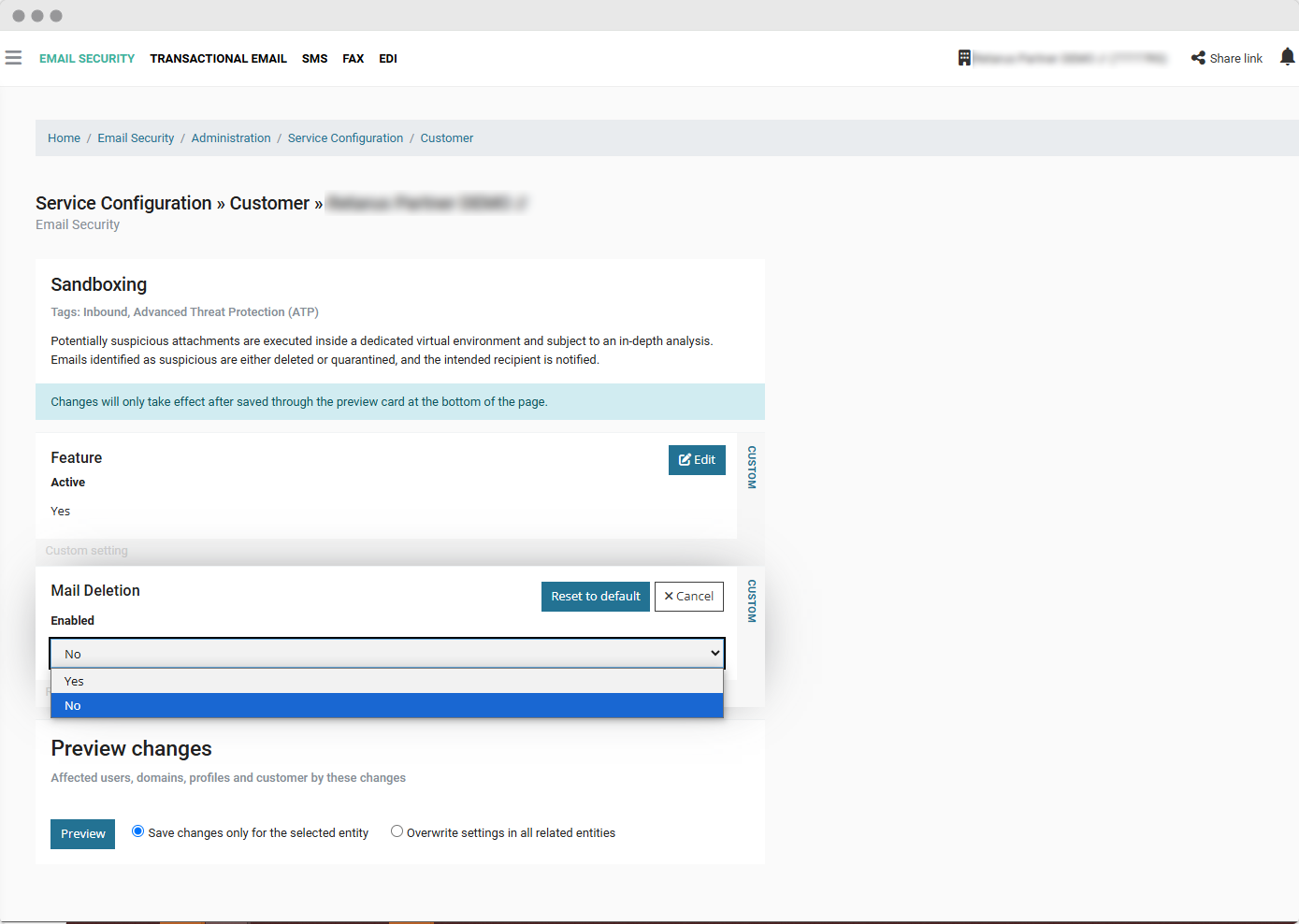
Wide-Ranging Detection Technologies
Intelligent Pre-filtering
Global Analysis with No Backchannel
The Retarus Advantage
Rule-Based Quarantine
Reporting and Monitoring
Networked Security
Customer Ratings and Reviews
Features
- Reputation Analysis
- URL extraction from files
- Anti-malware checking
- Wide range of supported file types: Compressed, Office and HTML
- Machine Learning, neural networks and behavioral analytics
- Advanced Anti-evasion mechanisms
- IOCs and MITRE reporting
- Custom Hypervisor
- Reputation Analysis
- URL extraction from files
- Anti-malware checking
- Wide range of supported file types: Compressed, Office and HTML
- Machine Learning, neural networks and behavioral analytics
- Advanced Anti-evasion mechanisms
- IOCs and MITRE reporting
- Custom Hypervisor
Thanks to leading sandbox technology, you always automatically benefit from cutting-edge machine learning approaches, neural networks and behavior analysis.
Globally networked threat intelligence, based on the analysis of trillions of files, enables the system to even detect novel threats quickly and precisely. This shared pool of data is continuously fed by thousands of companies, authorities and partners around the globe.
The result: AI models which are always up-to-date and continuously improving our detection technology – ensuring reliable protection for your email communication in real time.
- Private cloud sandbox – run entirely in the EU – contractually guaranteed
- Hash-based analysis – no personal content, such as files, recipients, subject lines or check results, is shared with third parties
- Certified security – ISO 27001 and SOC 2 Type II certified, with penetration testing on a regular basis
- Data minimization in practice – all data is deleted as soon as the analysis has been completed
- End-to-end encryption – for all transmission and file systems
Retarus Email Security: The European Advantage
Full-Service Cloud Offering
Truly European, No Compromises
Enterprise Expertise Since 1992
Real People, Real Support
What's Next?
Frequently Asked Questions
Which file types are analyzed by the sandbox?
The sandbox checks a wide variety of file types, including executable files, office documents, PDFs and compressed archive files. Even if data extensions have been manipulated, the sandbox recognizes the actual data type to be analyzed.
How long does it take for a file to be analyzed in the sandbox?
The duration of file analysis varies but is under four minutes in most cases. Checking especially large or complex files, for instance in archives, could take a little longer. Our intelligent pre-filter function assesses the benefit of using sandbox analysis in advance and only forwards emails where sandboxing adds real value. In this way, optimum performance is maintained while assuring security.
Which anti-evasion techniques are used?
With our AI-powered sandboxing, we rely on state-of-the-art approaches to prevent malware from recognizing the analysis environment and adapting its behavior. This includes mechanisms to safeguard against detection of virtual environments as well as methods to expose ploys to delay harmful behavior.
Can the sandbox also analyze URLs contained in emails?
Yes, the sandbox checks URLs embedded in emails by opening the linked content in a secure environment and examining it for harmful behavior.