Our email security experts have detected a rise in a sophisticated social engineering variant targeting companies, particularly their HR or payroll teams, with a scam that is difficult to detect at first glance.
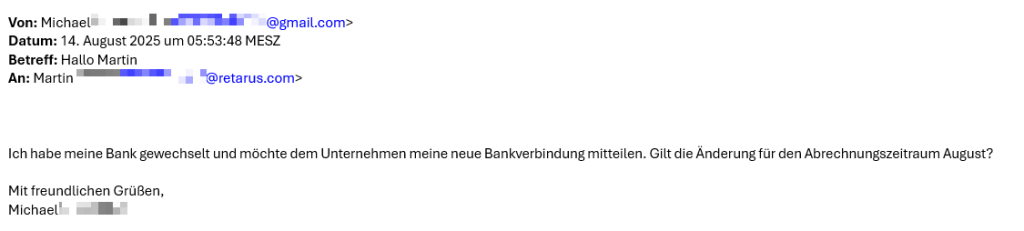
Alleged former employee sends new banking details
The modus operandi usually follows an identical course. Attackers use publicly accessible career networking platforms such as LinkedIn to research the details of individuals who, according to their profiles, have until recently been employed at the targeted company or have just started in a new position.
Using a private address which appears legitimate from a technical perspective (e.g., Gmail or Yahoo), the attackers then send a message to the HR or payroll department at the person’s previous employer.
The mail generally purports that the former employee has changed their banking details and therefore requests that all open payments (e.g., salary, bonus, overtime or vacation payouts) be transferred to the new account.
In follow-up messages, the scammers apply time pressure – typical for such attacks – or threaten the company with legal action.
For the recipient in the company’s HR or payroll department, the scenario seems entirely plausible at first glance, especially because former employees tend to use private email accounts rather than business addresses for such matters.
Why conventional checks often prove insufficient
This has an impact on the technical detection options available. Email security solutions often concentrate on detecting fake sender addresses, for instance via SPF, DKIM, DMARC and block lists, as a first line of defense. In these cases, however, we’re not dealing with typical domain spoofing (meaning a phony sender address) but rather with an address from a free email provider, which by its very nature has no connection with a corporate email domain. This makes it substantially more difficult to detect an attack based only on sender authenticity.
That’s why it’s essential that companies rely on a state-of-the-art email security solution which additionally employs AI-powered heuristics and pattern recognition.
Increasing the security awareness of staff remains another key line of defense
Raising the awareness of staff regarding security risks of course continues to play a vital role. Employees should constantly be reminded to always question the validity of emails, even when they seem plausible.
In the context of daily business, this means in practice:
- Not every email demanding payment is legitimate, even when it appears to come from a “real” or known colleague.
- The awareness of those working in HR, payroll or finance departments needs to be particularly high and substantiated by way of testing mechanisms following clearly defined procedures. Viable approaches include setting up internal guidelines to safeguard payment processes and imposing multiple checks and controls when it comes to authorizing payments. Under no circumstances should money ever be transferred based merely on having received an email.
Any change in payment or account details should always be confirmed by contacting the sender via another channel (e.g., telephone, cell phone number) and never by responding to the email itself.
To find out more about the wide-ranging protection mechanisms Retarus Email Security provides, feel free to get in touch with us.




