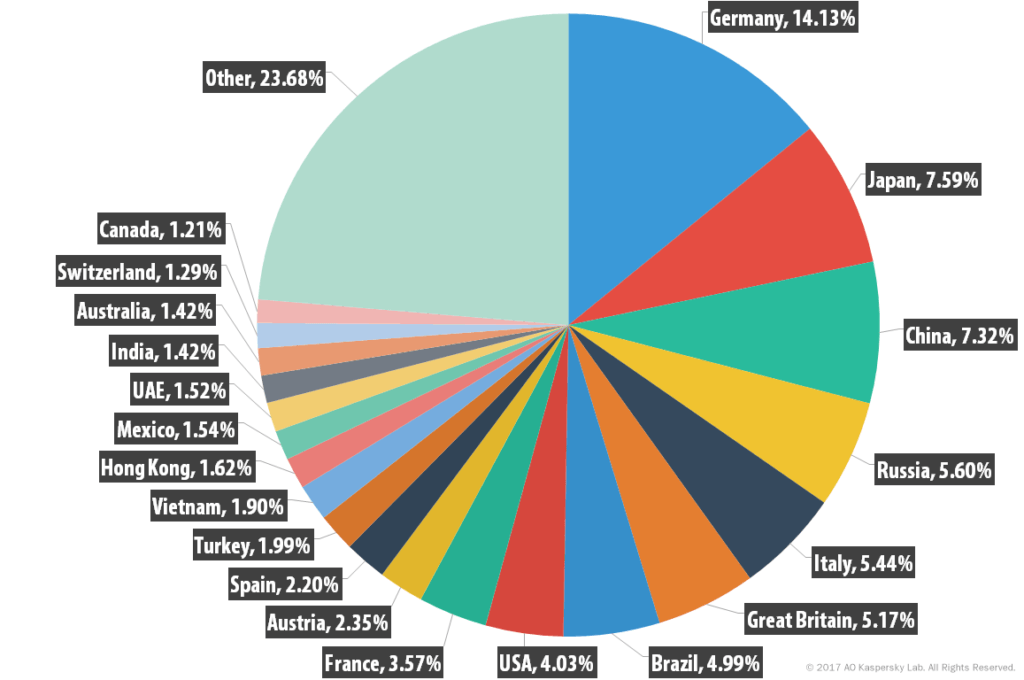
Russian IT security company Kaspersky Lab has released a very detailed analysis of global spam traffic in 2016. A core message of the annual report published on the Securelist blog is that the highest proportion of harmful spam emails (14.13 percent) was once again addressed to users in Germany. Nevertheless, the proportion fell by 4.93 percentage points in comparison with the 2015 figures. By contrast, a significant rise was registered in spam containing malicious code going to Japan and China in 2016. In the previous year, both of the pacific countries still placed well outside of the top 10. Germany is not as much in the firing line when it comes to phishing attacks. Here, Kaspersky systems measured Germany’s share of the total at 5.69 percent, placing it sixth amongst all countries. The five countries most often addressed with phishing emails, incidentally, were Russia, Brazil, the USA, China and Italy.
In total, Kaspersky Lab classified 58.31 percent of emails sent last year as spam (towards the end of the year the proportion had actually risen quite substantially), which was about 3 percent higher than in 2015. Around 12 percent of all spam emails were sent from the US, while Germany – with 3.21 percent (down 1.03 percent) – came in tenth. In 2016 a “huge amount of malicious spam” was registered, the Kaspersky authors go on to say, the largest part of which actually consisted of “Trojan downloaders that download ransomware to the victim’s computer”. The clear leading role played by ransomware may well be linked to the easy availability of such malware on the black market. It is mainly concealed in JavaScript or Java-coded trojans often in archives (but also less common formats such as CAB), however there were also office documents containing macros and classic, executable EXE files. Equally interesting are the methods and tricks used by spammers to give each email in a mass transmission the semblance of uniqueness. The random sequence of characters secretly littered around email messages is hidden ever more deviously. The spammers also go about camouflaging the links in the message by means of “noise” in remarkably tricky ways. Phishers, on the other hand, are increasingly employing services to delete the referrer. The last time that we saw a rise in the proportion of spam in all email communication was eight years back (in 2009). Since then the share of unwanted messages has continually decreased from a peak of 85.2 percent down to 55.28 percent in 2015. Kaspersky explains this primarily through the trend for small and medium-sized businesses to change over from using spam to other, legal marketing platforms. The slight increase now noted in 2016 is ascribed to the enormous amount of spam messages with attachments containing malware. The experts also hold such messages responsible for the rise in the proportion of medium-sized spam mails (between 5 and 50 kilobytes). Malicious spam containing ransomware is not expected to fall in 2017, Kaspersky estimates, in part because such programs are relatively easy to obtain on the black market. Fraud schemes targeting clients of financial service providers can also be expected to increase in number. In order to increase the reach of fraudulent sites, online criminals are now also going far beyond email and using all available media such as SMS, marketing and social networks to get in touch with potential victims. To safeguard against ransomware and other malware, companies of all sizes can complement running an up-to-date virus scanner on their end points by protecting their email inboxes with a managed cloud service such as Retarus E-Mail Security. Our brand new “Patient Zero Detection®” option can even determine after the fact, which recipients were already delivered messages containing malware (because they were new and thus still unknown). You can find out more details directly from your local Retarus contact person.Germans receive the most malicious spam

Tags: Email Security // Patient Zero Detection // Ransomware