In recent days, many inboxes have been receiving emails that at first sight appear to carry joyous news. In the subject line they announce a tax refund, and the sender seems to be “Her Majesty’s Revenue and Customs” (HMRC) – the British tax authority. So every recipient with business ties to the United Kingdom is likely to take a closer look.
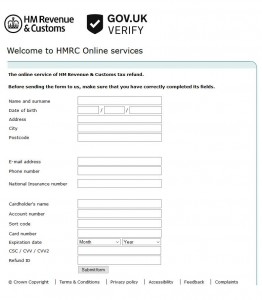
Fake form bearing the royal coat of arms
In order to benefit from the refund, the user is requested to click on a link – as is typical with phishing emails. The link leads to a convincingly deceptive replica of the British authority website – including an online form. However, the royal emblem at the head of this web form should in no way mislead users to provide the personal details that are being requested (name, address, insurance number, credit card details).
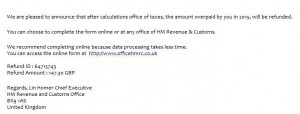
The real HMRC warns of fake emails
As the real authority communicates on their own website, such personal details are as a rule not requested via email, neither are tax refunds announced in this way. The HMRC lists a whole raft of fraudulent activities and expressly warns that such emails in some cases even include correct sender email addresses belonging to the authority.
Correct address details are no proof of authenticity
Basically, neither a correct sender address nor the right address or telephone details of the recipient should be considered to indicate that such emails are authentic. In comparable waves of phishing, attackers have been able to use correct addresses and personal details to mislead recipients. Also, such messages are increasingly accurate in their resemblance of the original messages, both in terms of their content and appearance. The language is correctly formulated and the messages contain authentic logos, fonts and colors.
How users and administrators can protect themselves
In addition to dependable security solutions with constantly up-to-date spam and virus protection, an increased level of user vigilance and alert plausibility monitoring is essential. Within a business environment, companies should therefore sensitize employees on how to deal with suspect emails. Irrespective of specific threats – the following basic tips should always be considered:
- Due to the remarkable similarity of phishing emails to the original messages, it is all the more important to carefully check the destination address contained in the link. The link can be checked by mousing over the clickable text prior to actually clicking on it. When in doubt, it is recommended to type the web address of the purported sender manually in the browser and log in to the secure customer or user area there. The authenticity of a website can also be checked via the lock icon in the web browser’s address line.
- Email attachments should basically only be opened when the email appears to be trustworthy, the sender is known and the procedure described in the email is customary.
- Even email addresses that at first sight appear to be correct should not be considered to indicate that a message is authentic. The addresses shown in the email client can also be manipulated with relatively little effort by online criminals. In cases of uncertainty, it is always best to check back with the supposed sender directly (by phone).
- Many viruses or ransomware such as “Locky” are spread via macros in email attachments. Many IT security solutions offer administrators the option of generally blocking potentially dangerous file attachments according to defined criteria.
- Many attackers find their way into systems through so-called “back doors”. These gateways are created by security gaps in operating systems and software. Users and administrators thus should keep all their systems up to date at all times. This includes installing operating system patches without fail and updating office applications, internet browsers, the flash player and PDF readers.
- Professional security solutions additionally boost protection against phishing attacks. Specialized cloud service providers such as Retarus continuously add to their filter rules and use several virus scanners to increase the probability of also recognizing new threats reliably. Mechanisms to safeguard the system, such as web security filters, also prevent users from accidentally opening phishing sites.