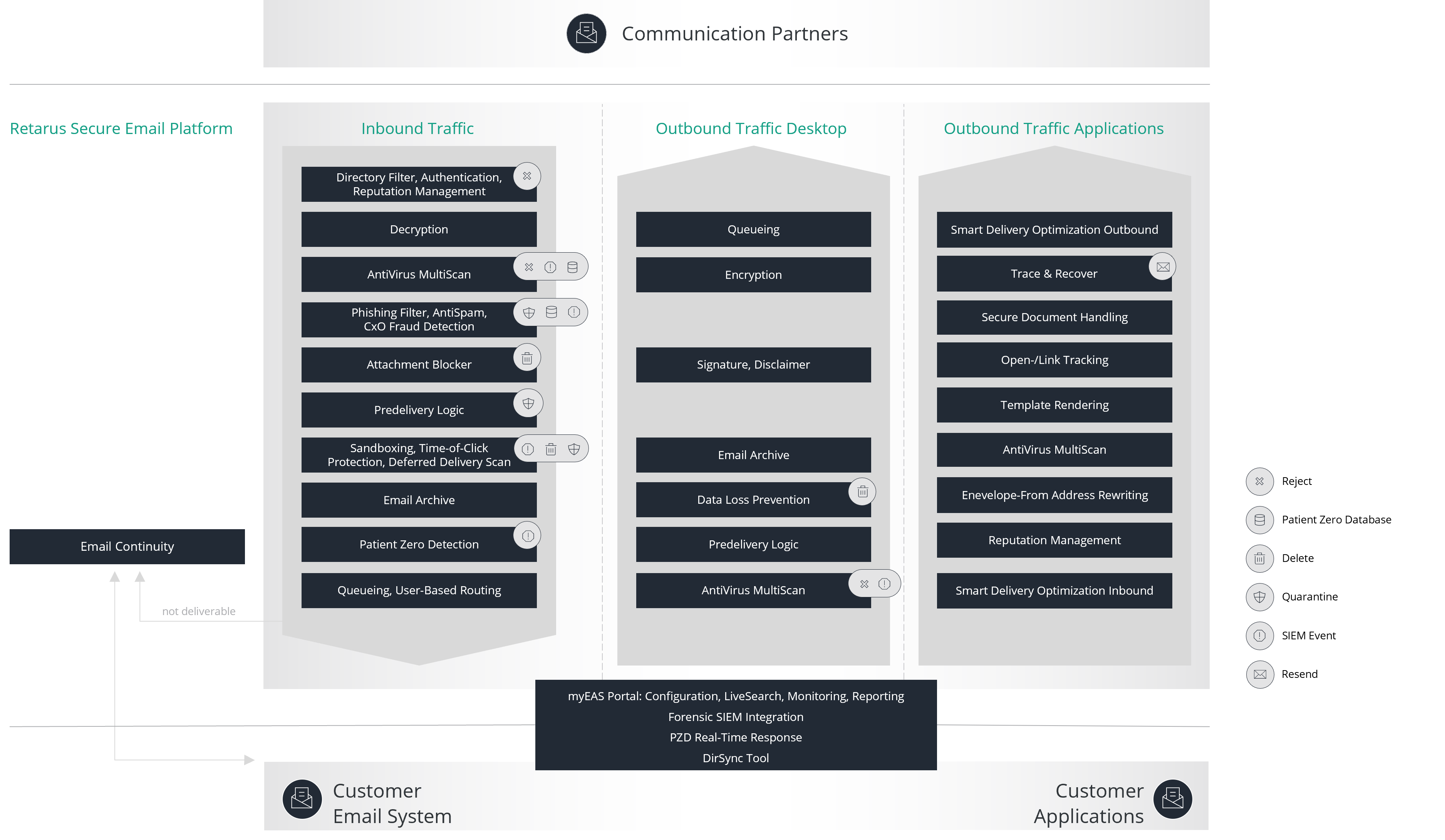
Secure Email PlatformTechnical Specifications
The comprehensive solution for virus- and spam-free email communication: offering gateway-based encryption, data processing in Retarus data centers according to local data protection regulations, innovative email management, and tamper-proof archiving.
General Features
General Features
Access Management
With Access Management in the Retarus Enterprise Administration Services Portal (Retarus EAS Portal), access rights for administrators can be assigned flexibly and according to requirements for e.g. countries, subsidiaries, domains, or departments.
- Granular, hierarchical rights concept for administrators
- Flexible assignment of access rights to e.g. configurations and evaluations
Directory Synchronization
In addition to manually maintaining addresses in the Retarus EAS Portal, Automated Directory Synchronization can reconcile addresses automatically with the customer's address book and directory services.
- Reconciliation of address books and directory services from Microsoft (Exchange, Active Directory, Azure Active Directory (AAD) for Microsoft 365), HCL Notes Domino and LDAP (Directory Synchronization)
- Reduction of manual administration and maintenance
- Immediate update of data pool in the Directory Filter
- Increased protection from directory harvesting attacks
- Local management of export address data by the customer
Monitoring & Reporting
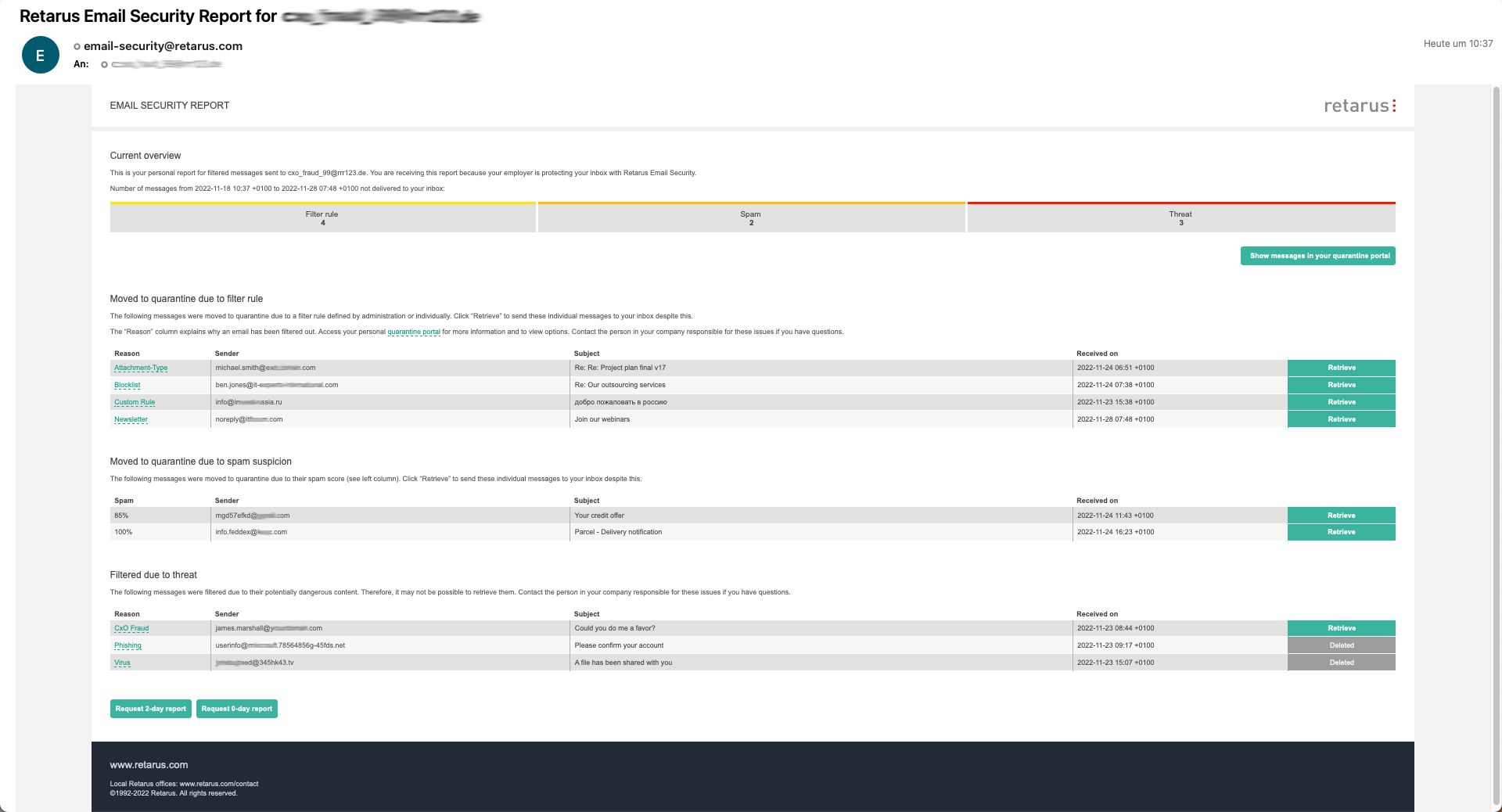
In addition to easy management of service instances and user profiles 24/7, the web-based Retarus Enterprise Administration Services Portal (Retarus EAS Portal) offers information about the effectiveness of Retarus Email Security Services. All reporting and monitoring information can be downloaded in a prepared format, offering process transparency that is unique to the market.
- Transparent display of all service features
- Management of service and all additional Retarus services
- Detailed reports and powerful analysis functions
- Performance monitoring
- Email Live Search – tracking of all incoming and outgoing emails in real time
- Setup and management of user profiles
- Individual management rights for administrators via Access Management
- Support ticket creation and tracking
- Documentation
- Secure access via web browser
Encrypted Connection to Retarus
Maximum protection of customer data: customer systems are connected via TLS (Transport Layer Security) or optional VPN (Virtual Private Network) to the Retarus Enterprise Cloud. This makes it impossible to read data exchanged between customers and the Retarus infrastructure even with today's level of technology.
- Connection of customer systems via opportunistic or enforced TLS possible
- Connection of customer systems via VPN possible
Email Cloud Gateway
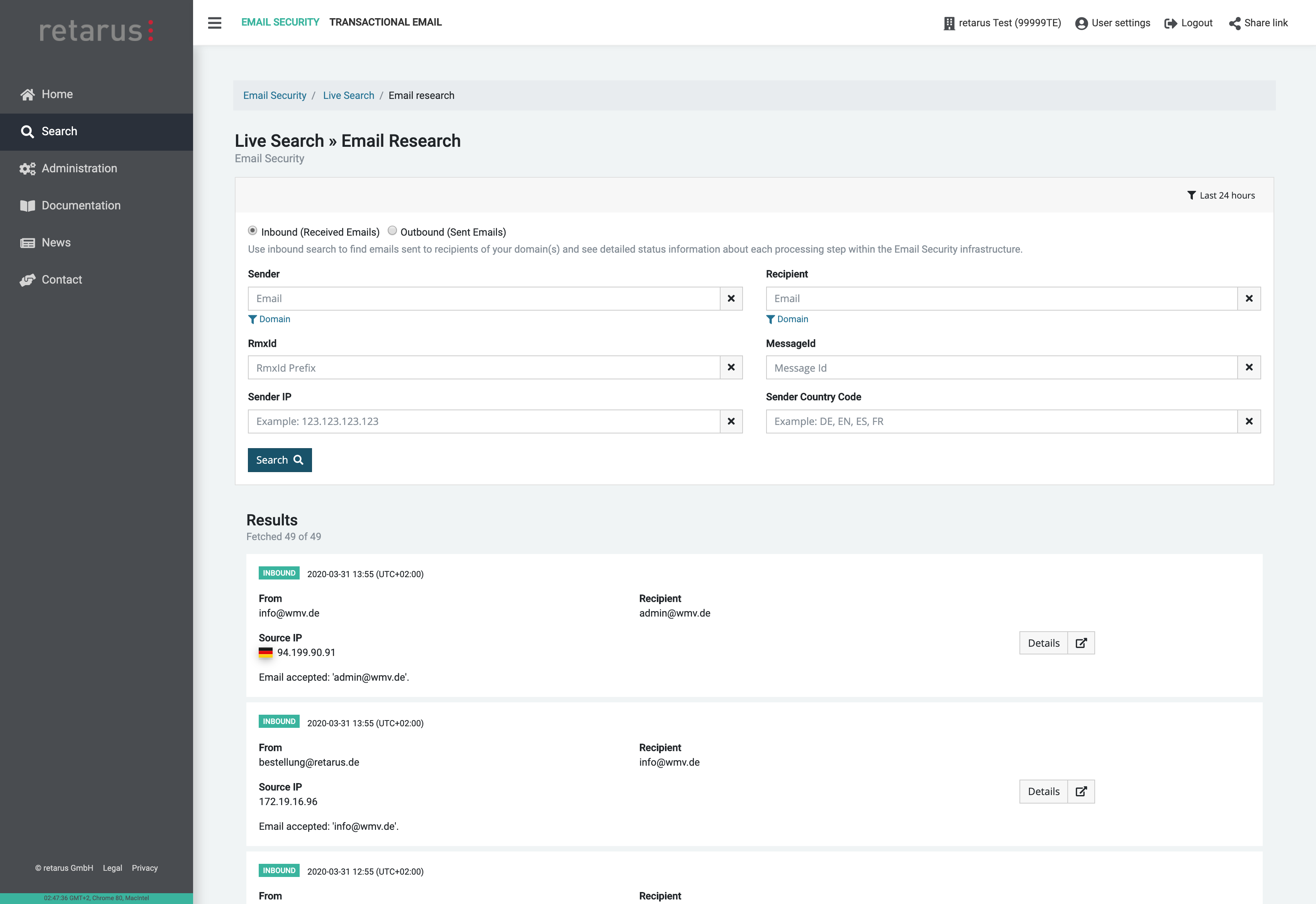
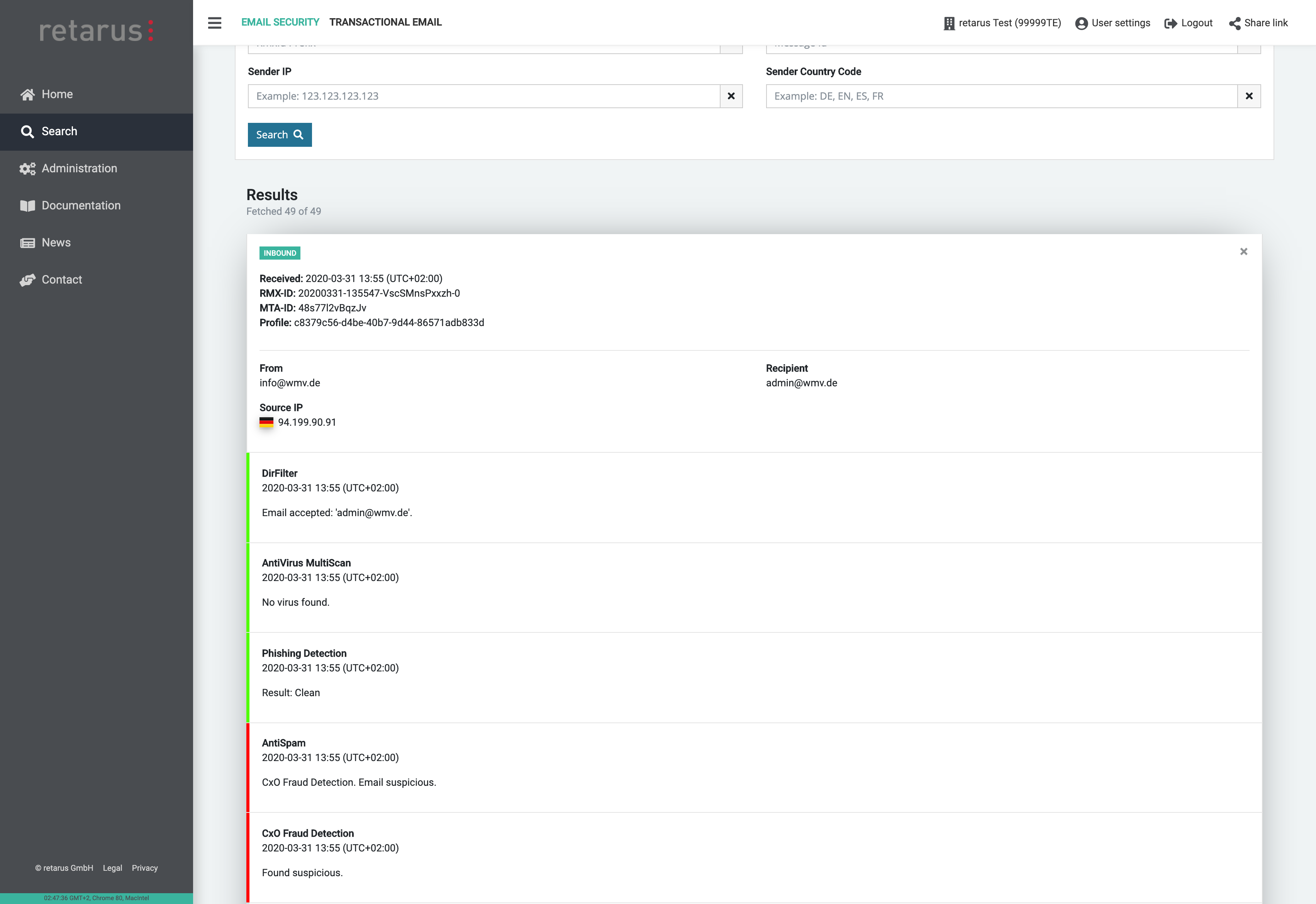
Email Live Search
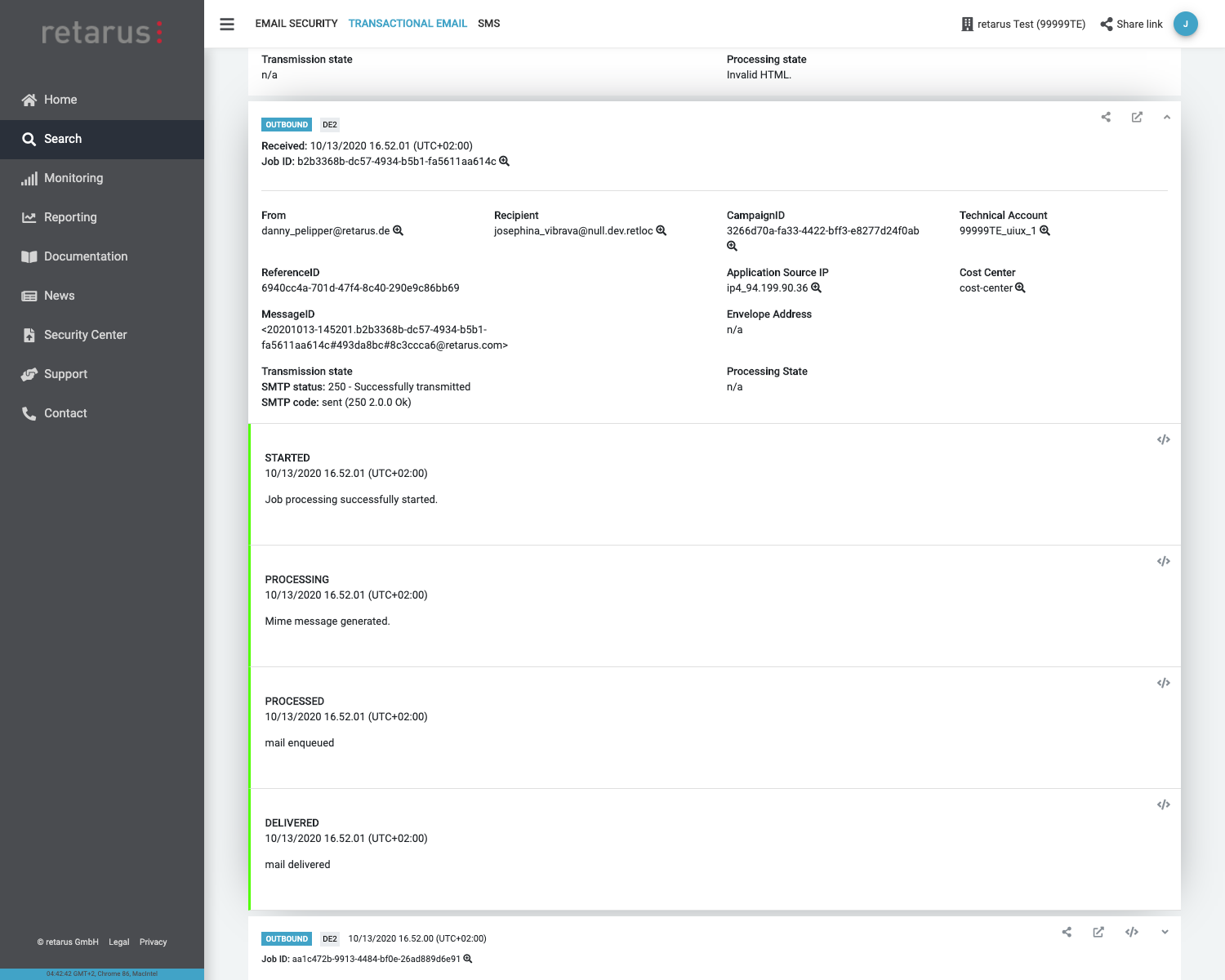
Email Live Search provides detailed results on the status of individual emails in real time. This search function makes it easier to find emails, simplifies the analysis of delivery delays, and supports IT forensics. For example, the help desk can release emails marked as graymail to users from within user guidance.
- Targeted search in real time for inbound and outbound emails
- Immediate display of the results list
- All information available for up to 45 days
- Direct access to emails placed in quarantine
- Clear information about throughput time
- Targeted search for message ID and source IP
- Detailed information about each Retarus Email Security step
- Information about malicious emails detected by Advanced Threat Protection (Deferred Delivery Scan, Time-of-Click Protection, CxO Fraud Detection)
- Information about emails detected by Sandboxing
- Information about emails detected by Patient Zero Detection®
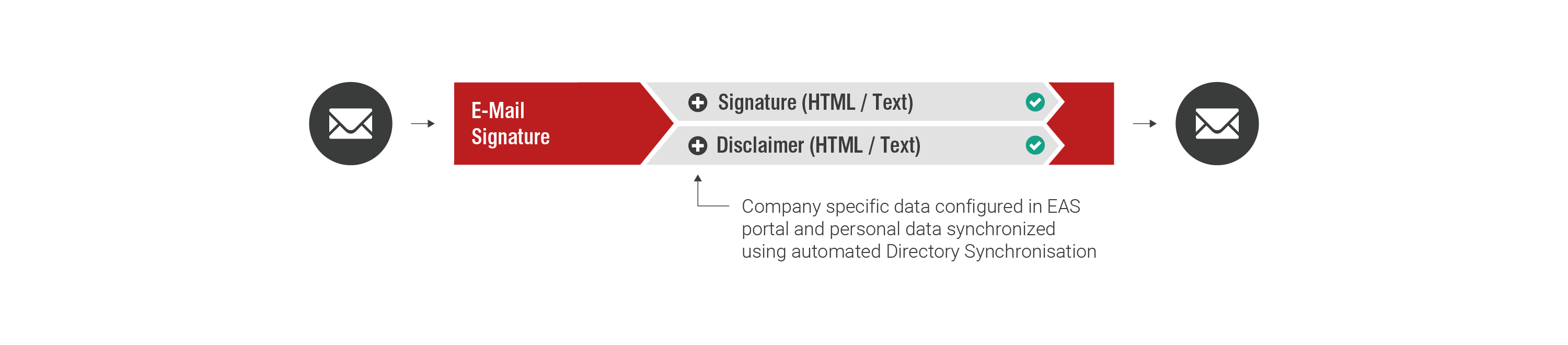
Email Signature
According to statutory requirements, business emails must contain signatures, just as they are required for customary business letters in commercial correspondence. Required information includes data that is often changed, such as telephone numbers. Retarus Email Signature helps create and centrally manage signatures and disclaimers quickly and efficiently.
- Centralized management of personalized email signatures and disclaimers
- Easy maintenance using the WYSIWYG editor in the EAS Portal
- Personalization directly via Active Directory or HCL Lotus Domino
- Signature and disclaimer assignment at the profile level
- Ability to combine any signature with any disclaimer
- Use of signatures in external emails only
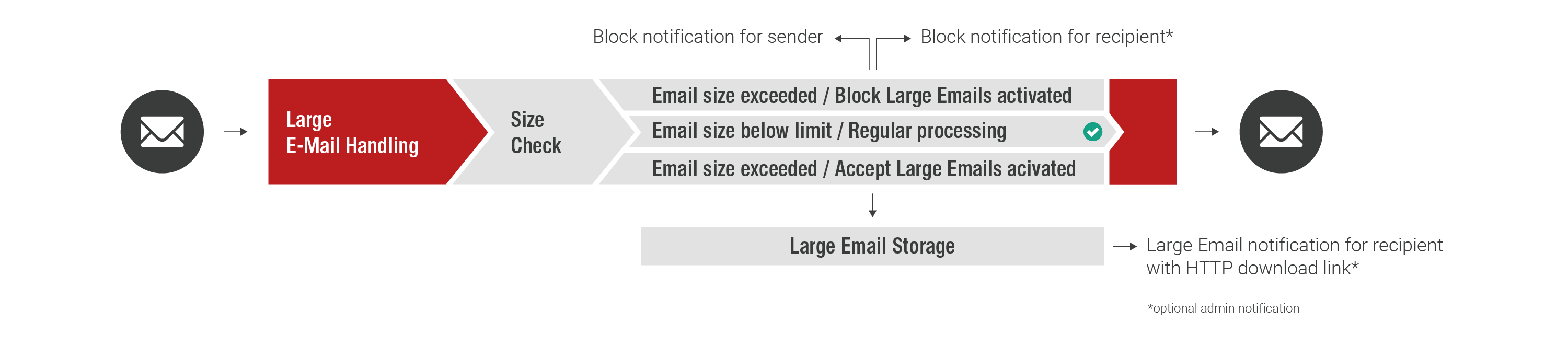
Large Email Handling
Retarus Large Email Handling allows you to reliably block emails above a defined size, or alternatively, depending on your settings, to store them securely in Retarus' own datacenters. In the latter case, the recipient is notified by email and may release affected messages individually. This way, sensitive messages of several megabytes in size, such as applications, balance sheet calculations, patent documents, design drawings or credit applications, reach their destination directly without detours via potentially insecure web-based filesharing services. At the same time, unwanted emails above a certain size are reliably blocked, thus significantly reducing the load on your company's email servers.
- Receive large emails regardless of size limitations
- Flexible configuration of size limitations at the company and profile level
- User access for downloading emails with simplified user authentication (OneClick token login)
- Lighter load for email infrastructure and backup systems
- Quicker restore times, reduction in storage costs
- Consistent implementation of email policies
- No dependencies on potentially insecure web-based filesharing services
User-based Routing
Within the scope of User-Based Routing, Retarus delivers emails for specified recipients (user-based) within a domain to specific target servers.
- Recipient-based relaying to configurable MTAs
- Ideal solution for migration scenarios or complex infrastructures
Email Security
Essential Protection
AntiSpam Management
AntiSpam Management runs spam checks of incoming emails using rules and tools that are continuously updated. Depending on the service setting, emails classified as spam are flagged or quarantined.
- Spam protection with an identification rate of over 99.95%
- False positive rate of less than 0.0001%
- Protection from mass non-delivery notifications (backscatter protection)
- Blocklists and allowlists at the user, profile, domain, and global level
- Multi-lingual content analysis
- Content and structure analyses using heuristic methods
- Upstream "bad word" filter to meet compliance policies
- Fingerprint analysis, Bayes algorithms, sender check
- Continuous updating of intelligent filter, pattern, and identification rules
Similar to scanning incoming messages, AntiSpam Management Outbound uses the same filter technology to prevent the (unintentional) distribution of spam messages. In this way, you not only protect the recipients of emails, but also the reputation of your company and your sender domain.
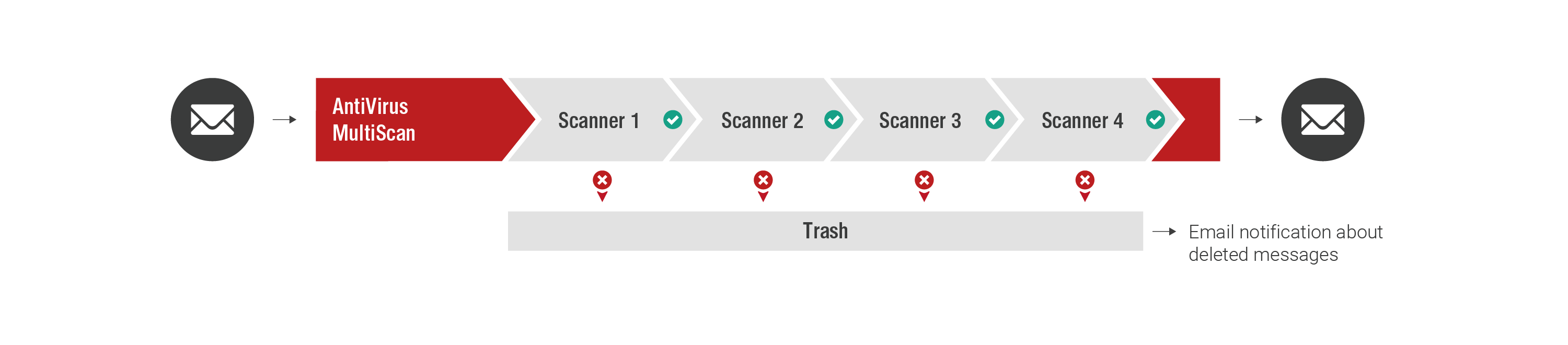
AntiVirus MultiScan (2x)
AntiVirus MultiScan (2x) automatically scans incoming and outgoing emails and file attachments for viruses with two different virus scanners and uses heuristic analysis to protect from unknown malware.
- Higher identification rate with two virus scanners
- Protection from unknown viruses using heuristic analysis (Zero-Hour Protection)
- Elimination of threats before they reach your infrastructure
- Continuous updating of virus definitions
- Notification of deleted infected emails via an email security report (email digest)
Want more protection? In addition to other benefits, Advanced Threat Protection also offers higher identification rates thanks to using four different virus scanners.
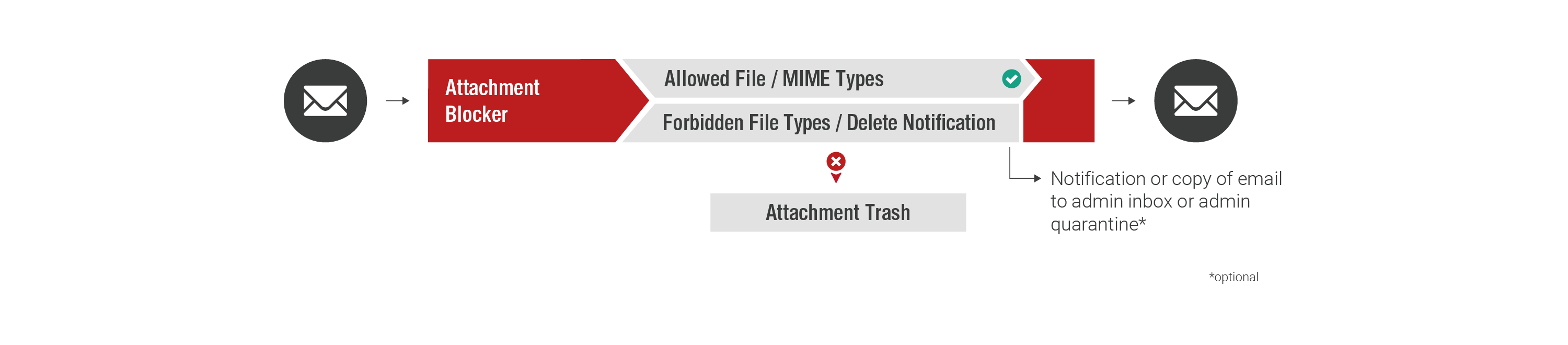
Attachment Blocker
The Attachment Blocker prevents the receipt of attachments which should have been prevented from reaching the company infrastructure. For example: .exe, .zip, or Office files with macros. The files to be blocked can be defined by the customer.
- Block undesired email attachments
- Define files to be blocked using file extensions or the MIME type
- Automatically block nested or password-protected archives and unknown MIME types
- Configurable message options for recipients regarding deleted attachments
- Ability to deliver copies of the original emails to administrators
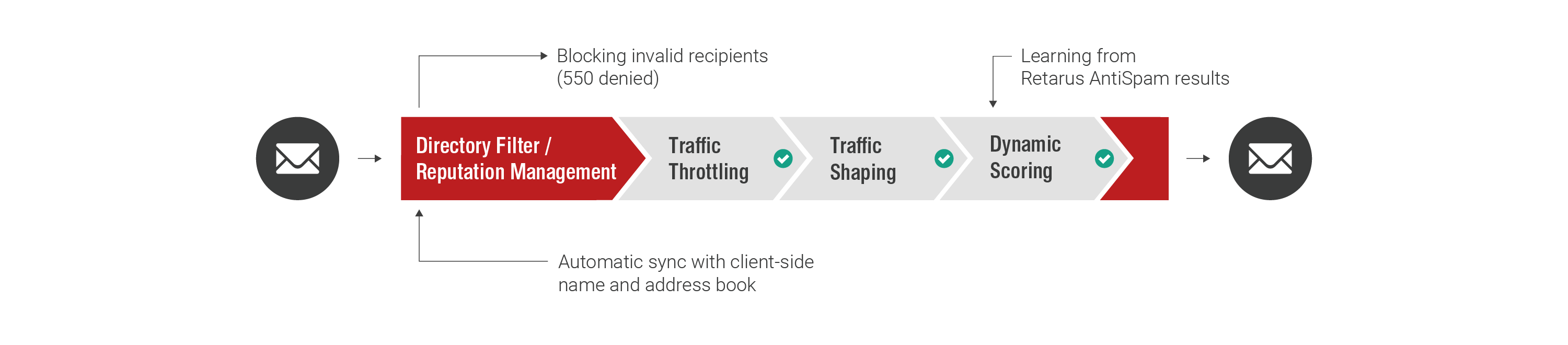
Directory Filter
The Directory Filter rejects incorrectly addressed emails in accordance with RFC. As a result, the processing time of incoming and outgoing emails is reduced significantly. Valid addresses are automatically and regularly synchronized with your systems.
Furthermore, emails from senders that are conspicuous - due to attempted denial of service and directory harvesting attacks - are subjected to a separate classification process and accepted with delay (traffic throttling mechanisms).
- Protection from denial-of-service and directory-harvesting attacks
- Inbound Reputation Management – traffic shaping and traffic throttling mechanisms
- A service that learns dynamically with scoring/penalty system for spam relays
- Queueless design with checks on the SMTP session level
- Automatic address book synchronization with Microsoft Exchange, Lotus Notes/Domino, LDAP
- Address book synchronization in time intervals defined by the user
- Provisions for alias names and other domains
- Bounce management according to RFC 3461, 3463, and 3464
- Configuration and manual address entry via the Retarus EAS portal
- View in Retarus Email Live Search Monitoring (Tracking Point)
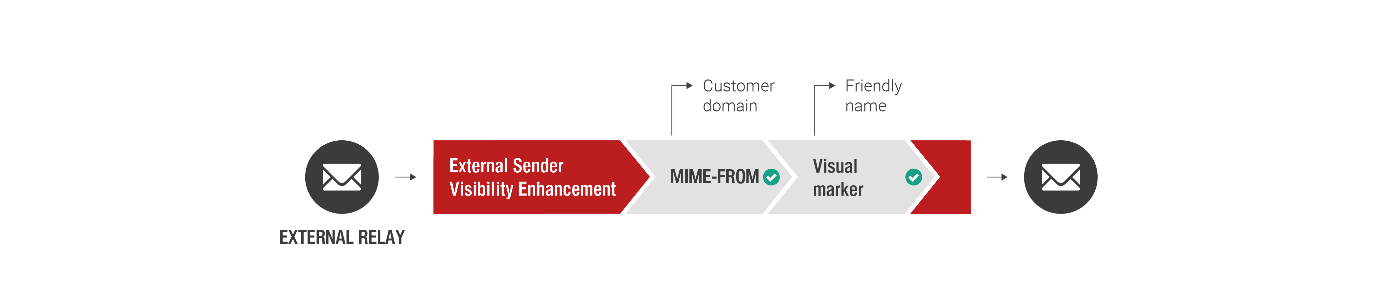
External Sender Visibility Enhancement
In addition to applying Directory Filter functions, incoming emails are checked for the reputation of their senders. Senders are authorized through validation of the SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). Classified emails that do not pass validation are isolated in a quarantine.
- Validation of incoming emails (external relay) that use your domain in the sender address (MIME-FROM)
- Flagging of suspicious emails with visual indicators such as pre-defined Unicode characters at the beginning of the sender field (friendly name); alternative free text also possible
Inbound Reputation Management
Inbound Reputation Management supplements the Directory Filter checking the reputation of the senders of incoming emails. Email authorization depends on whether the verification functions SPF (Sender Policy Framework),DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting and Conformance) are validated. Classified emails that do not pass validation are e.g. isolated in a quarantine.
- Email Authentication – SPF and DKIM and DMARC validation
- Notification of potentially affected emails via Email Security report (Email Digest)
- Configuration via the Retarus EAS Portal
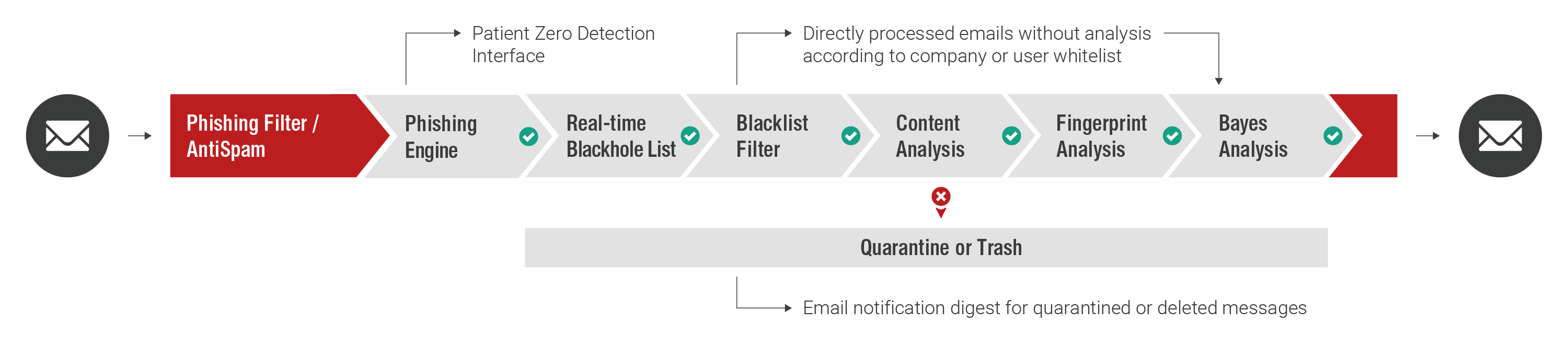
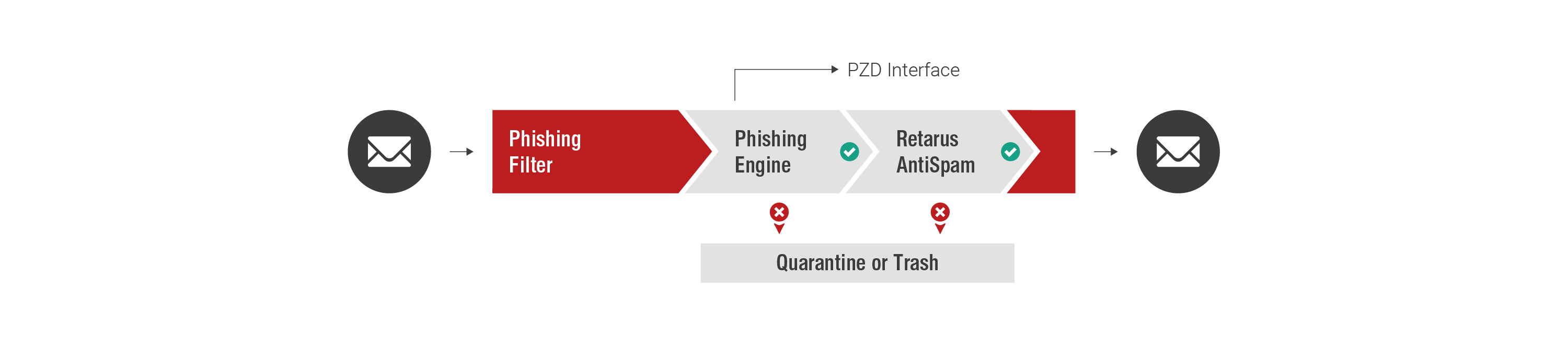
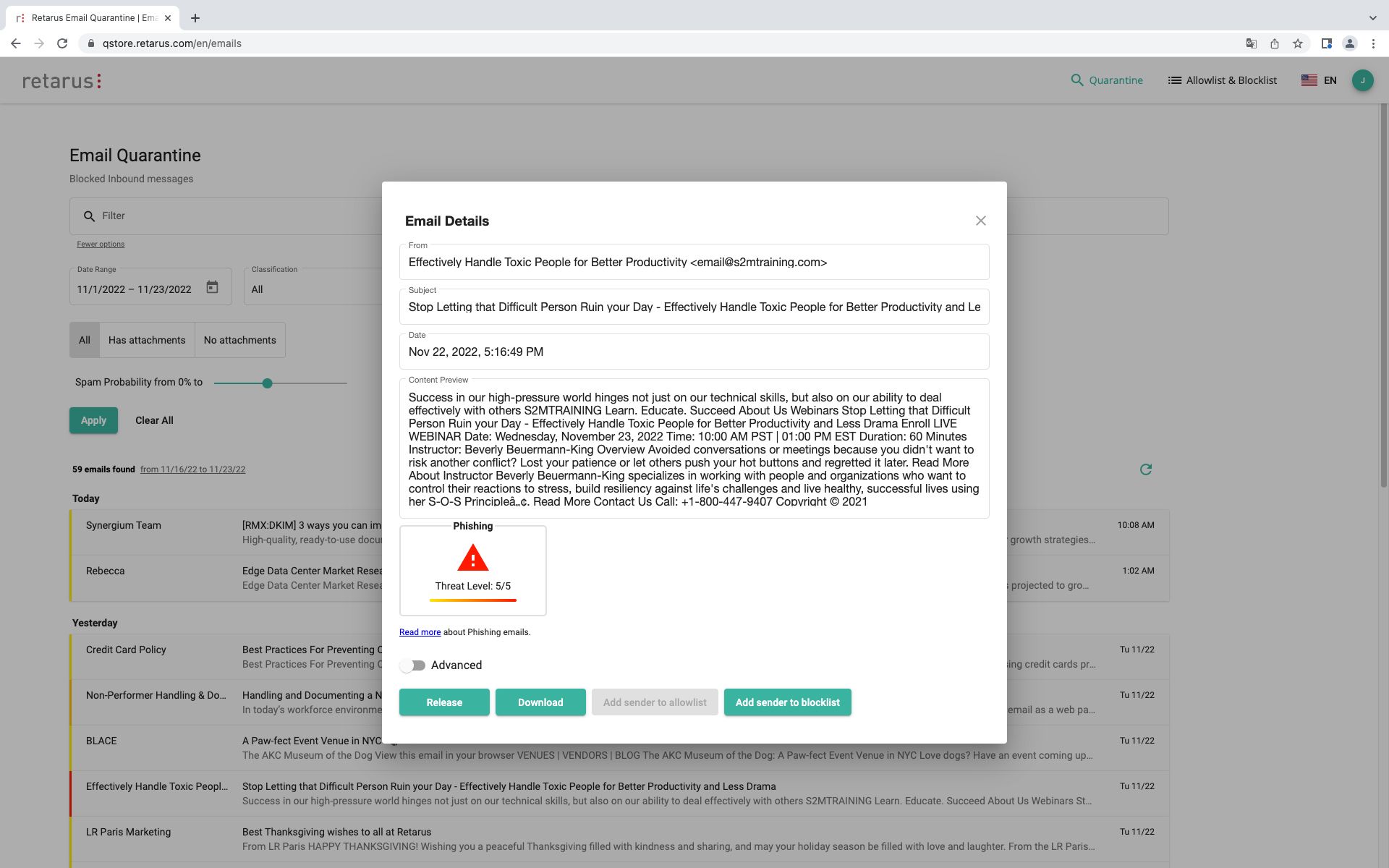
Phishing Filter
The Phishing Filter scans incoming emails in real time for phishing scams. Those in question are either moved to quarantine and flagged as “phishing” or immediately deleted.
- Detects phishing emails that are not yet caught by the virus scanner or spam filter
- Query of several databases of renowned specialized providers
- Quarantine option or immediate deletion (configuration in EAS Portal)
Similar to scanning incoming messages, Phishing Filter Outbound uses the same filter technology to prevent the (unintentional) distribution of phishing messages. In this way, you not only protect the recipients of emails, but also the reputation of your company and your sender domain.
Would you like to further protect yourself and render phishing links harmless, even in emails that have already been delivered? Then supplement your Essential Protection with Retarus Time-of-Click Protection and functionalities such as URL rewriting and real-time checks of web links.
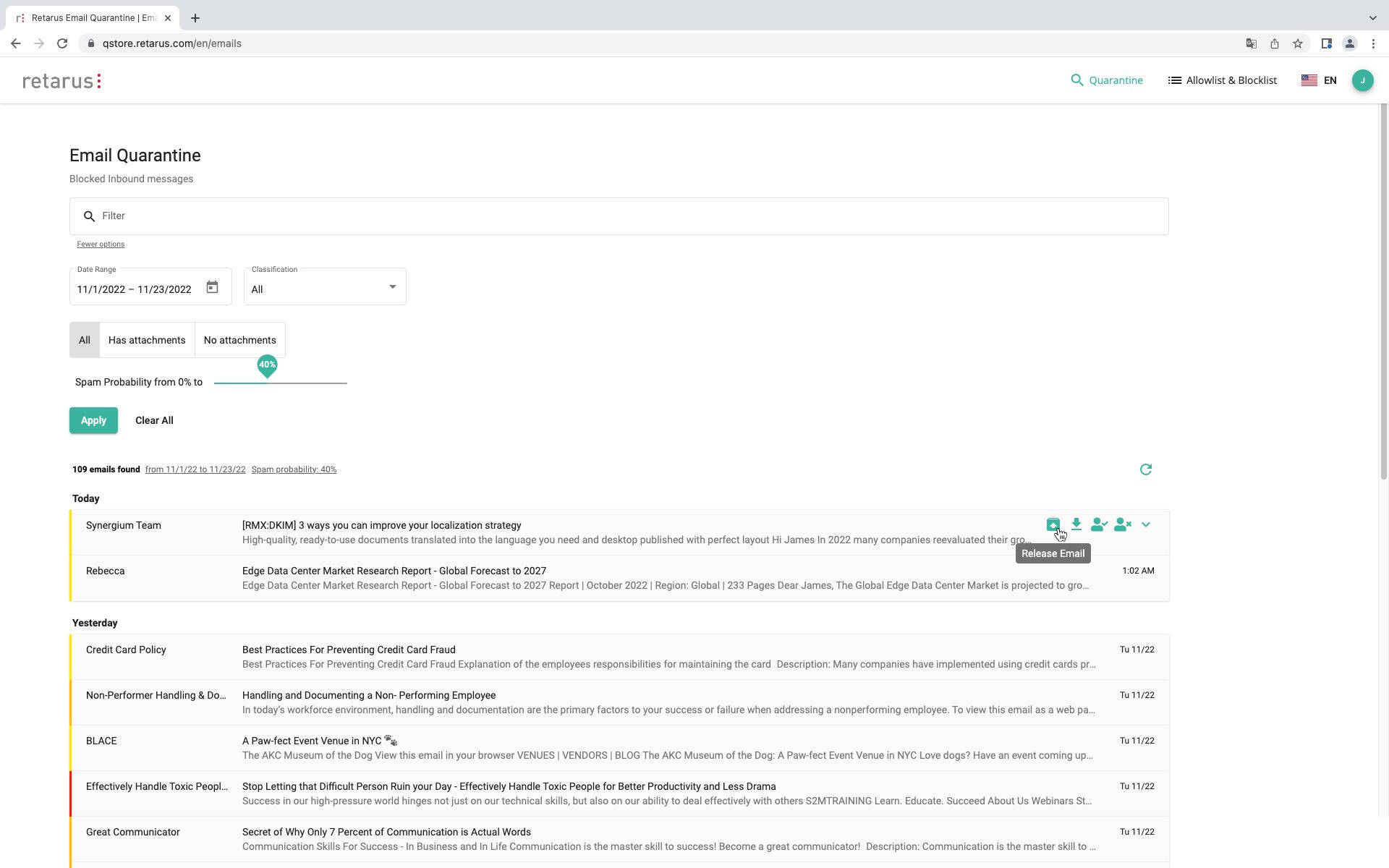
Quarantine Management
Simplified email handling for employees and administrators. At customizable points in time, reports sent by email (Email Digests) offer a quick view of the emails flagged for deletion or quarantine by Retarus Email Security components.
- Clearly structured reports on undelivered emails (spam, viruses, phishing, newsletters, etc.) via email
- Combined overview of spam, viruses, and graymail via email
- Online access with simplified user authentication (OneClick token login)
- Direct access to quarantined emails classified as spam
- Additional virus scan after retrieval from quarantine
- Advanced search for quarantined emails, e.g., depending on attachments or classification
- Color bar visualization for instant recognition of threat level
- Detailed view including additional information on each email
- Support for mobile devices
- User-based quarantine and report settings
- System-wide configuration via the EAS Portal for administrators
- Multi-lingual: Available in 11 languages for best end user education
Outbound Recipient Restriction
This capability is aimed at preventing identity exposure, and facilitating efficient administration.
The Recipient Restriction feature empowers you to set a custom maximum number of recipients (0-600) for outbound emails. Exceeding the configured limit can trigger rejection, temporary failure, or silent discard based on your preferences. The feature may be configured on all hierarchy levels (customer, domain, profile, user).
Outbound Size Restriction
By default, outbound emails processed by Retarus may have a size of up to 250 MB. With the Outbound Size Restriction function, you can limit this value even further to reduce the load on your infrastructure.
Exceeding the configured limit can trigger rejection, temporary failure, or silent discard based on your preferences. The feature may be configured on all hierarchy levels (customer, domain, profile, user).
Advanced Threat Protection
Extended AntiVirus MultiScan (4x)
AntiVirus MultiScan (4x) automatically scans incoming and outgoing messages as well as file attachments for viruses with up to four independent virus scanners. This increases the virus detection rate significantly when compared to Essential Protection. Using heuristic analyses, malware that is still unknown can be identified.
- Higher identification rate with up to four virus scanners
- Protection from unknown viruses using heuristic analysis (Zero-Hour Protection)
- Elimination of threats before they reach your infrastructure
- Continuous updating of virus definitions
- Notification of deleted infected emails via an email security report (Email Digest)
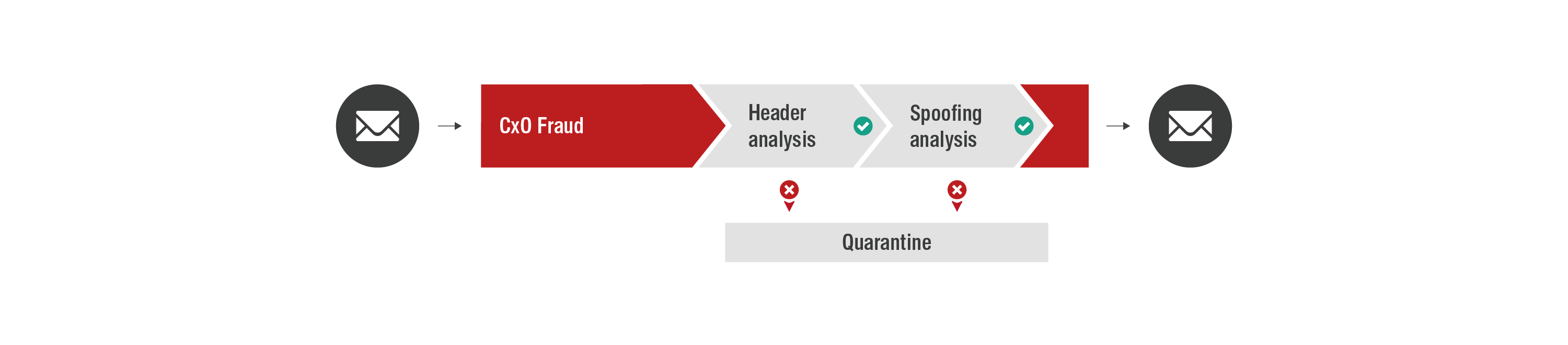
CxO Fraud Detection
CxO Fraud Detection uses algorithms that identify from-spoofing and domain-spoofing, to detect falsified sender addresses (e.g. from high level executives). Emails identified as CxO fraud are not delivered immediately, but rather quarantined.
- Protection against emails with fake sender ("spoofing" or "impersonation attacks")
- Combination of different detection methods and algorithms:
- Analysis of header information
- Recognition of similar looking domains or character sets (domain similarity)
- Recognition of fake sender names, e.g. the CEO
- Delivery of legitimate external email secured via email authentication (SPF) and allowlisting
Deferred Delivery Scan
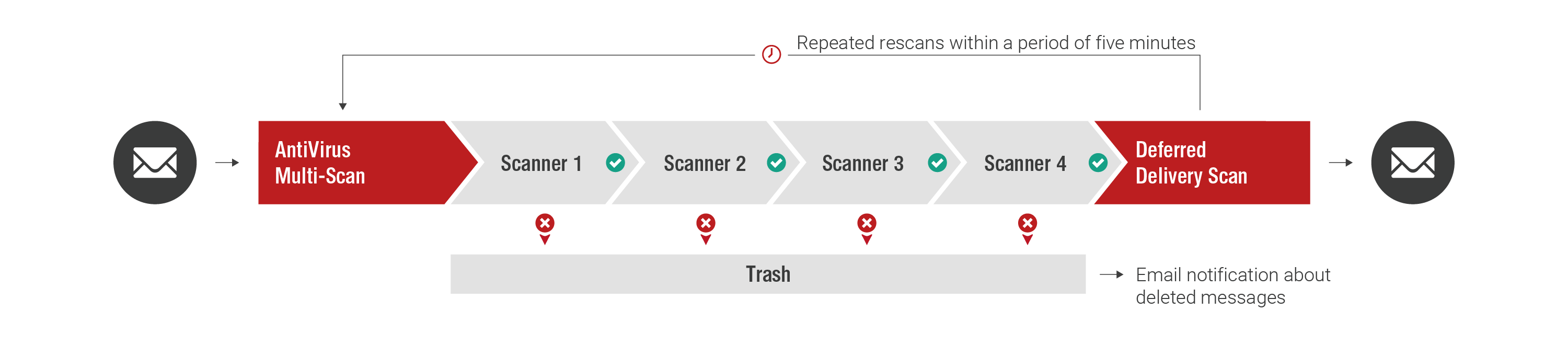
Higher identification rate due to additional re-scan procedures: As part of Deferred Delivery Scan (DDS), defined file attachments undergo further analysis using additional re-scan procedures. The delay means that signatures for the engines, which were not there at the time of the initial scan, could exist in the new malware at the time of the quadruple Retarus AntiVirus MultiScan rescan. DDS performs multiple re-scans within a short amount of time. If a virus is detected, Retarus deletes the affected files and informs the intended recipient.
- Effective re-scanning with quadruple Retarus AntiVirus MultiScan
- Protects from viruses that are unknown at the time
- Select view of advanced security checks in Retarus Email Live Search Monitoring (Tracking Point)
- Notification of infected emails via an email security report (Email Digest)
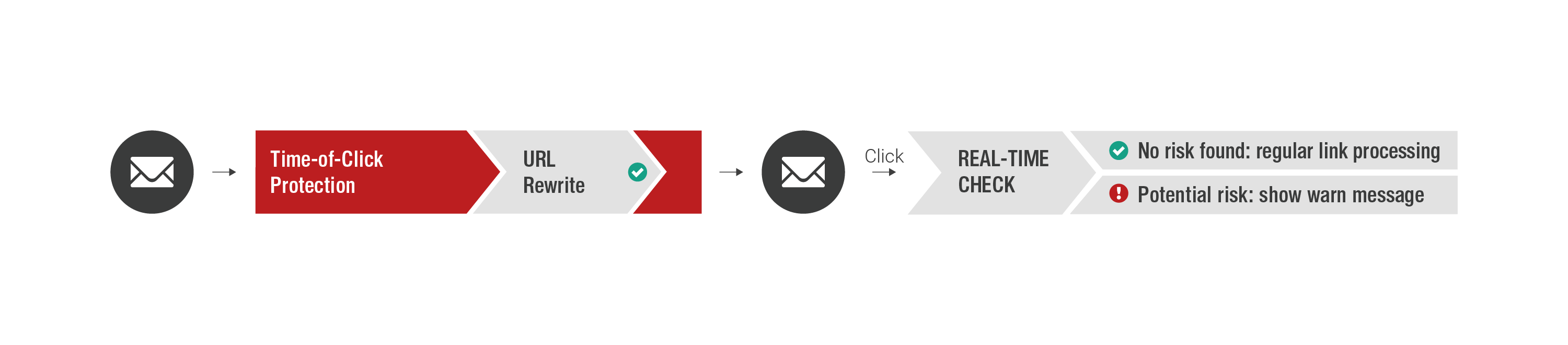
Time-of-Click Protection
Time-of-Click Protection automatically re-writes links (URLs) in emails (URL Rewriting). When recipients click on these links, the links are checked for suspected phishing target addresses. If the target site is not identified as a phishing site, the user is sent directly to it. If the target site is a phishing site, a security warning is issued.
- Real-time checks of web links in emails
- Expanded protection from phishing attacks
- Effective blocking of phishing websites and warnings for affected users
- Customer security warnings can be saved (custom design)
- Select view of advanced security checks in Retarus Email Live Search Monitoring (Tracking Point)
Post Delivery Protection
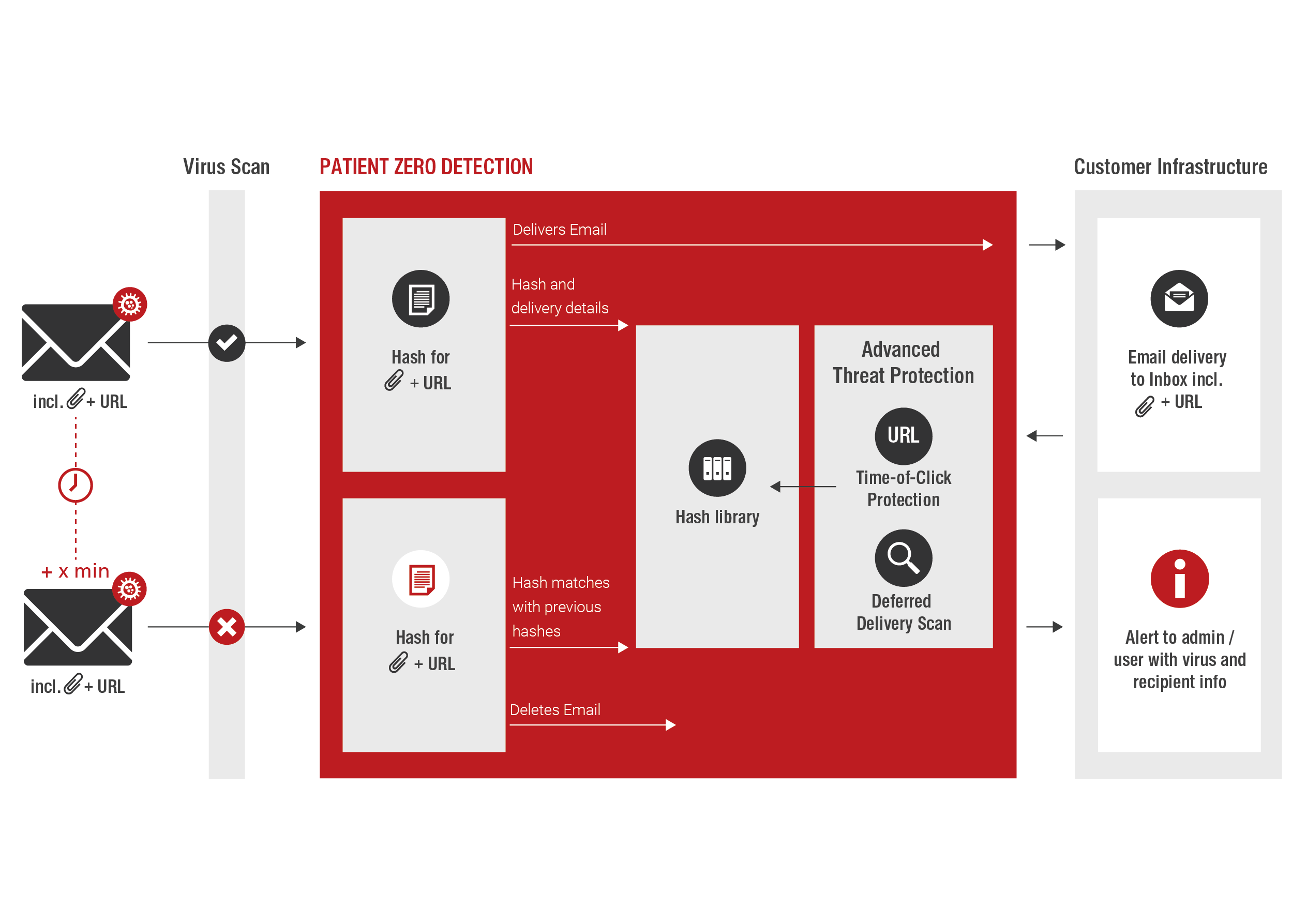
Patient Zero Detection®
A malware's signature is still unknown the first time it appears, even to the best virus scanners. In combination with 4-way AntiVirus MultiScan, Patient Zero Detection® uses a digital fingerprint to identify emails containing malware or phishing links that have already been delivered. Relevant alerts are sent according to customer settings. This way, appropriate defensive actions can be taken as quickly as possible.
- Identification of the recipient ("patient zero") of malicious emails already delivered using a digital fingerprint
- Alerts sent to administrators (to ensure a quick response)
- Simplified IT forensics
- Identification using content analysis together with advanced 4-way AntiVirus MultiScan
- Security Center in EAS Portal delivers additional values to PZD hash library
- Optional alerts sent to users
- Supports the optimization of security settings (e.g., blocklist entries)
- In-depth checks of email attachments by executing them in virtual machines
- Additional, automated learning from the Advanced Threat Protection results
- Cumulative reports for any given period of time
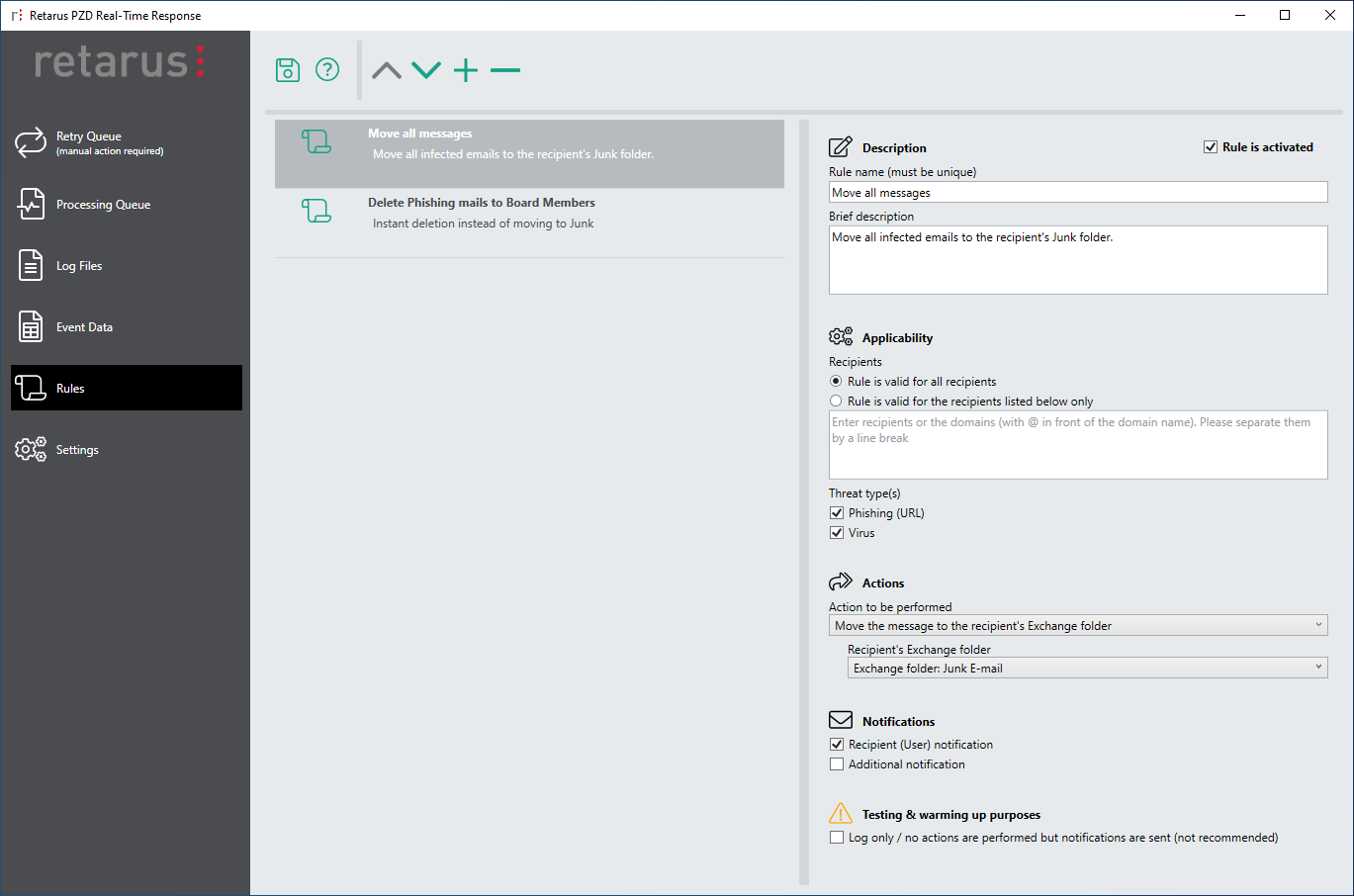
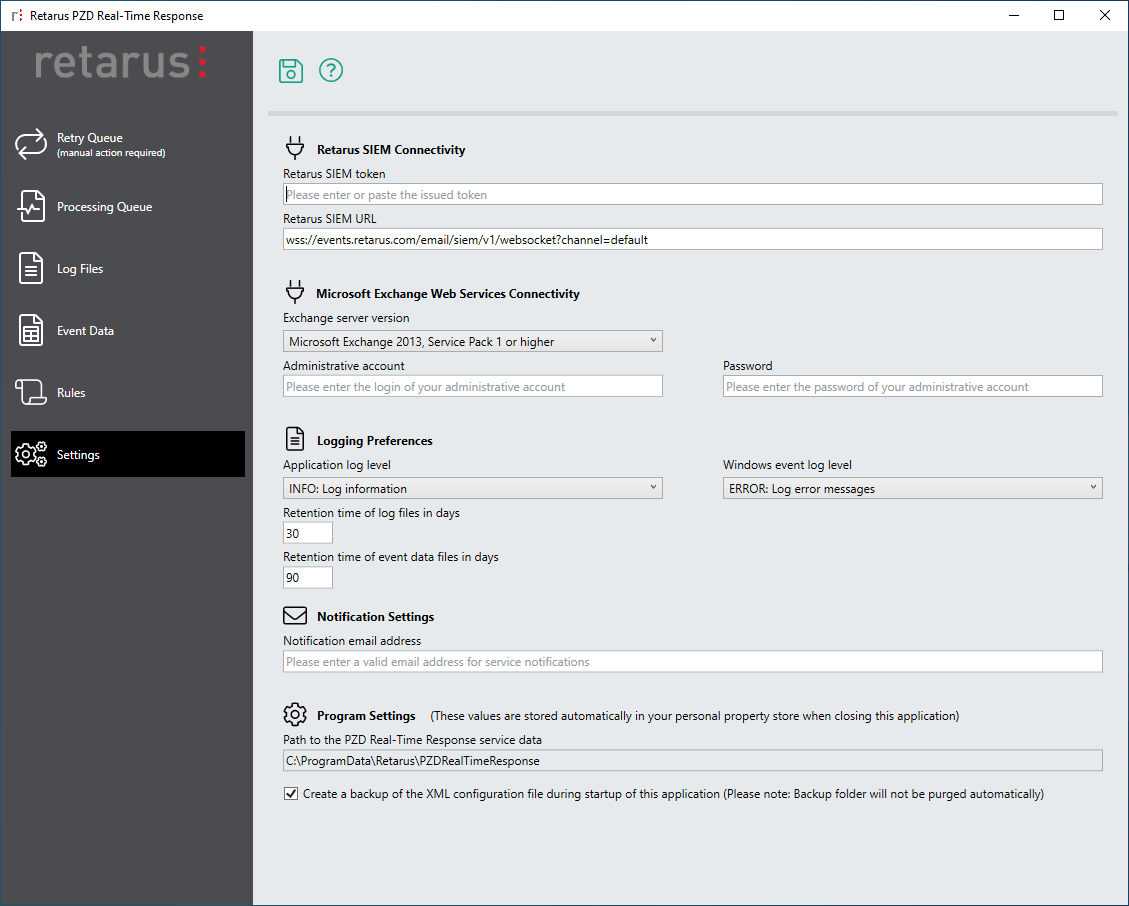
PZD Real-Time Response
Using Patient Zero Detection® Real-Time Response, Patient Zero Detection® results can be processed in a rule-based manner to identify and automatically move or delete potentially dangerous emails from a user's mailbox.
- Detailed, standardized information via administrator notification to support automatic processes used to remove emails from the server
- Configurable text for alerts (enables the distribution of behavior recommendations that are easy to understand and can be quickly implemented)
- Reduces the administrative work for IT forensics, support, and the help desk
- Increases the level of protection through immediate response to identified emails
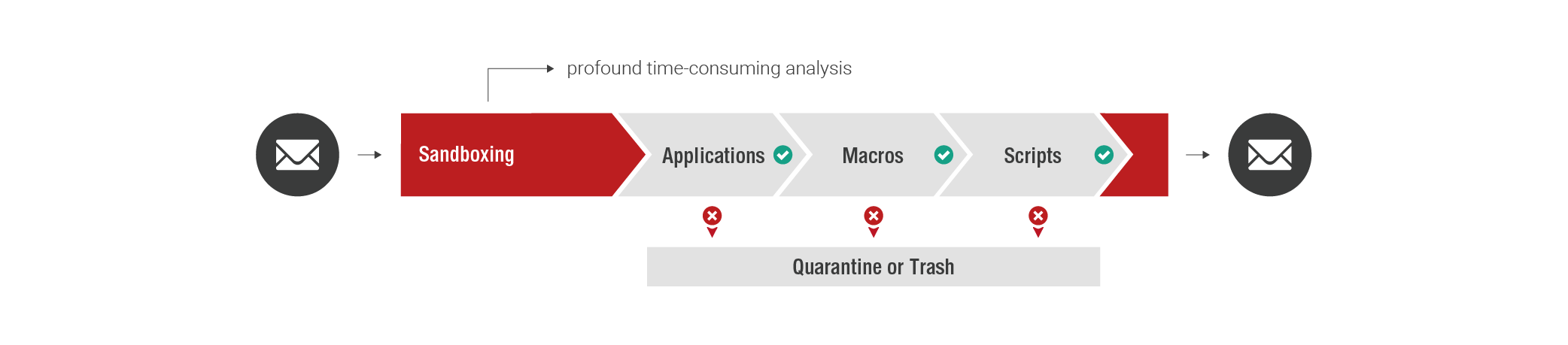
Sandboxing
Sandboxing
InboundOutbound
Sandboxing subjects specific file attachments to an in-depth analysis. Attachments that contain potentially malicious code (e.g. files and active elements) are exported to a virtual machine and checked for unusual behavior. For this advanced threat check, Retarus uses a leading third-party sandboxing technology. Emails identified as infected are either quarantined or deleted, and the intended recipient is notified.
- In-depth checks of email attachments by executing them in virtual machines
- State-of-the-art machine learning, neural networks, and behavioral analytics for fast, accurate detection
- Securely operated in Germany
- Each file submission immediately destroyed after scanning
- Certified with ISO 27001 and SOC 2 Type II
- All file systems used by the service are fully encrypted
- Notification of infected attachments via Email Security Report
- Select view of advanced security checks in Retarus Email Live Search Monitoring (Tracking Point)
Forensics
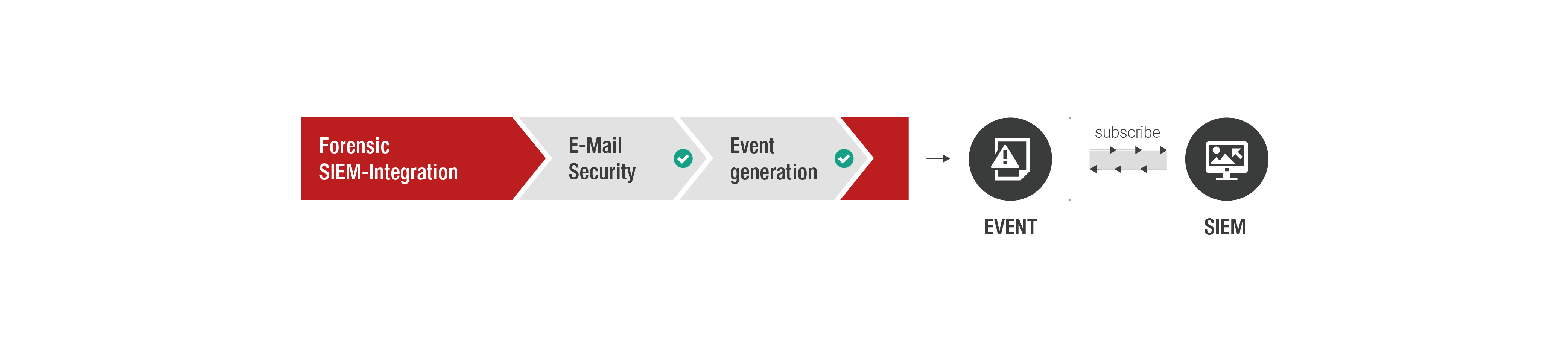
Forensic SIEM Integration
Forensic SIEM Integration offers events you can subscribe to that enrich your data stream with details about email security.
- Provisioning of real-time forensic data in the form of events
- Access via protected interface
- Subscription to security-relevant events from all SIEM tools customary in the market
- Currently available events:
- AntiVirus MultiScan Inbound and Outbound
- Sandboxing
- CxO Fraud Detection
- Patient Zero Detection®
- Inbound emails in general
- Outbound emails in general
Email Compliance
Email Archive
Email Archive
Retarus Email Archive stores incoming and outgoing email communication automatically, reliably, and long term. Archived messages are tamper-proof – they cannot be altered and are protected from unauthorized access. Messages and attachments can be found in a fraction of a second using powerful search functions that can be narrowed granularly according to different data protection requirements.
Comprehensive
Compliant
Secure
Email Encryption
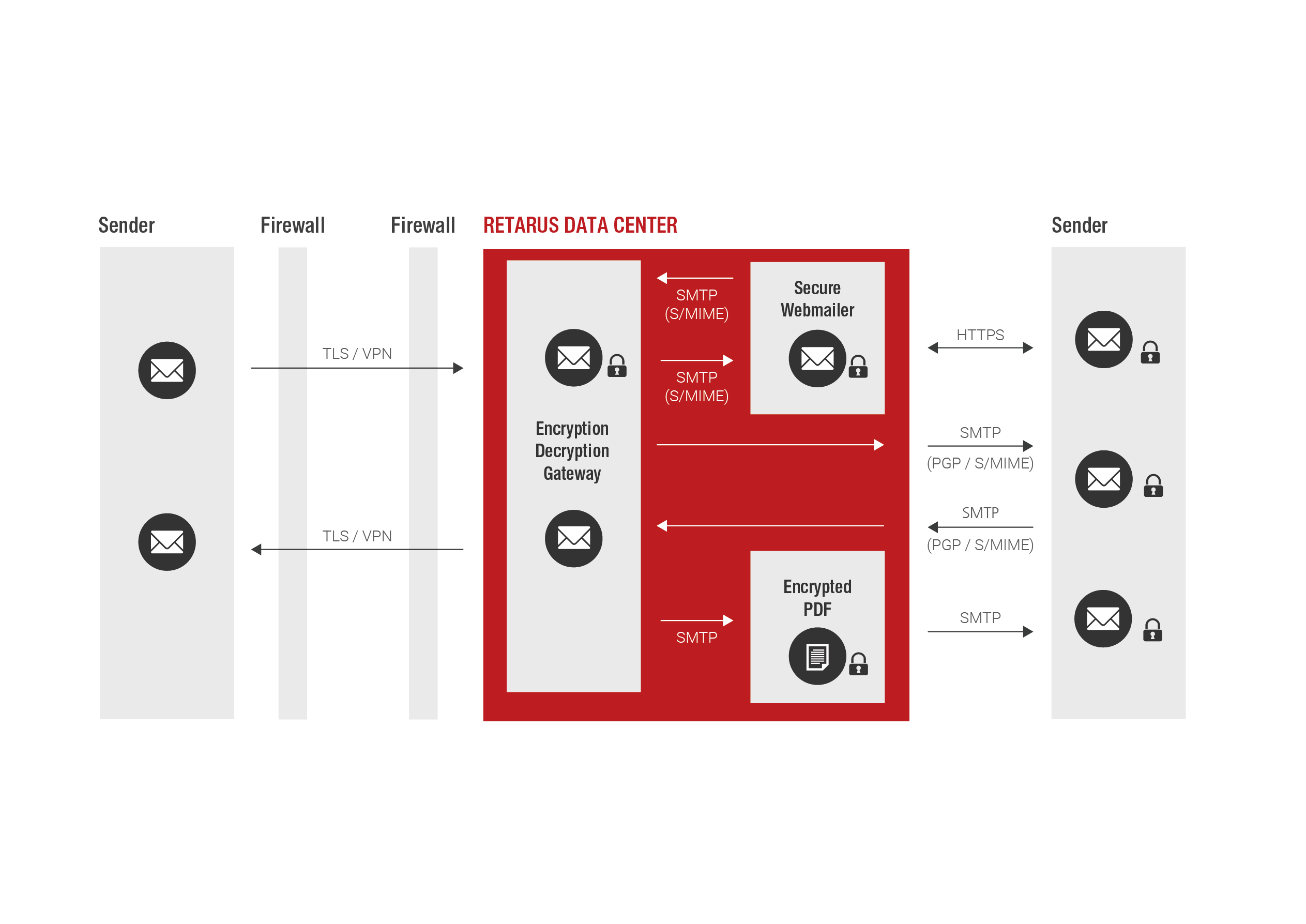
Email Encryption
Emails are identified in Retarus data centers, fully encrypted using customer-specific rules, signed as needed and sent securely to the recipient. This means that the email and all of its file attachments are encrypted.
- Compatible with any SMTP-based email system (e.g. Microsoft 365, Google Workspace, Microsoft Exchange, HCL Notes Domino)
- Complete key management by Retarus: create, distribute, and manage all keys
- Easy adoption of existing PKIs (public key infrastructures)
- Gateway-based S/MIME and PGP encryption
- Full support of the X.509 v3 standard including own certificates
- Full support of the OpenPGP standard
- Automatic or user-initiated signature of outgoing emails
- Ability to include internal company encryption policies
- Centralized and flexible set of rules for emails that need to be signed
- Filters for viruses and spam despite encryption
- TLS connection to the Retarus Enterprise Cloud
- Optional VPN connection for secure and confidential communication over the "last mile"
- Web email portal or password-protected PDF for encrypted communication with recipients without their own encryption solution
- Company-wide standardized solution that can be expanded as needed
- No software and hardware installation required
- User Synchronization for Encryption (USE) feature automates management of encryption users, groups, associated certificates/keys, as well as organization-specific policies.
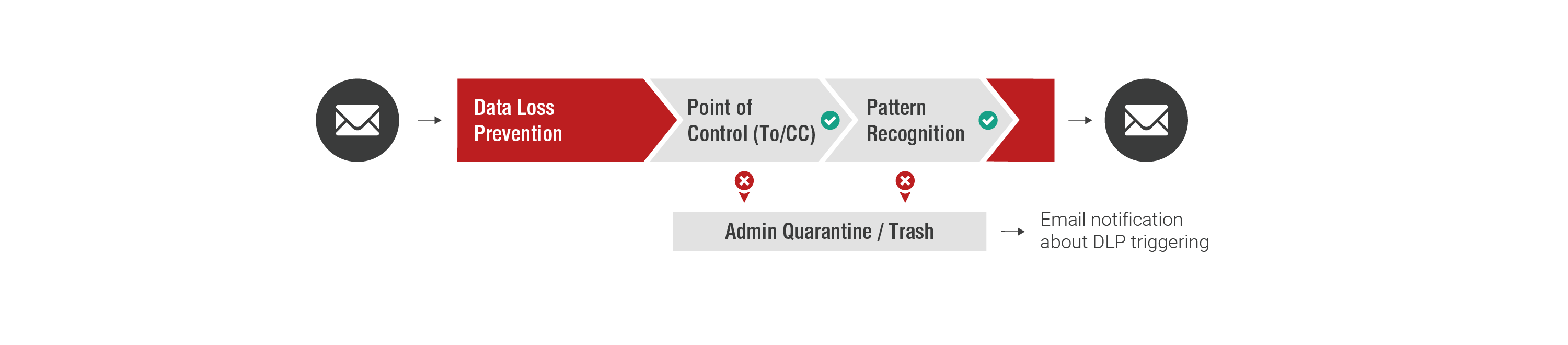
Data Loss Prevention
Data Loss Prevention
Data Loss Prevention (DLP) checks emails addressed to external recipients systematically for pre-defined criteria and helps you prevent loss of internal and confidential information.
If a delivery attempt is prevented, the sender immediately receives a message, and if configured, other employees (e.g., administrators, compliance officer) as well. Additionally, specific rules regarding permitted recipients can be defined at the mailbox level. The integrated attachment blocker also prevents the sending of defined files or file formats.
Comprehensive DLP functions offer advanced monitoring options and meet individual compliance requirements applicable to enterprise email communication.
- Definition of permitted senders/recipients per mailbox (defining required email addresses in the To:/Cc: fields as a monitoring entity for all outgoing messages)
- Attachment Blocker for all outgoing messages
- Definition of pattern recognition for potentially sensitive information in emails (e.g., credit card numbers or bank details (IBAN))
Transparent notifications and monitoring:
- Immediate notification of affected senders (optional notification of administrators or compliance officers; isolation of affected emails in quarantine)
- Select view of advanced security checks in Retarus Email Live Search Monitoring (Tracking Point)
Email Infrastructure
Transactional Email
API for Sending Emails from Applications
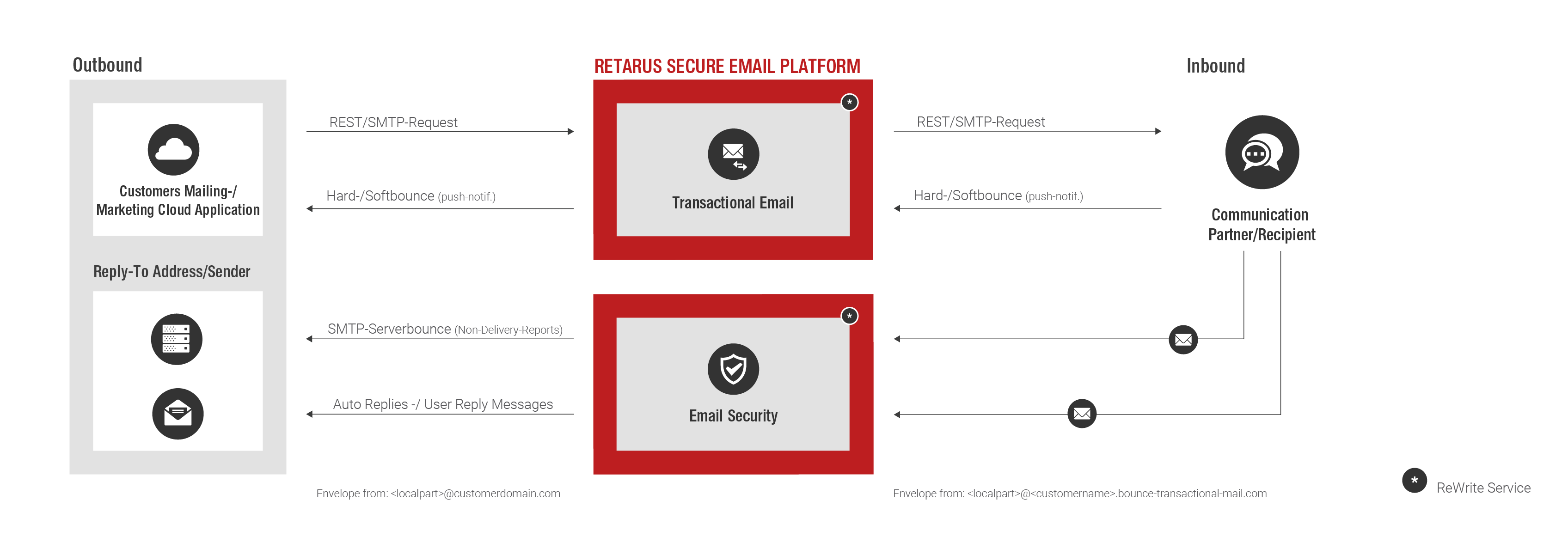
Retarus Transactional Email helps you send large volumes of email from your business applications (ERP and CRM systems) without impacting your own email infrastructure.
- Guaranteed processing capacity of up to 10 million emails per hour
- Permanently high, guaranteed throughput rate
- High availability and disaster recovery plan
- Global availability and local processing
- Detailed status notifications
- Above-average inbox placement rate
- Differentiation of transactional, marketing, and P2P emails possible
- No internal email infrastructure needed
- Connection via REST API and SMTP adapter
- Authentication via Auth Basic or source IP
- Encryption based on sender domain via enforced TLS
- Ensuring the authenticity and integrity of the sending system using DNSSEC
- Check performed by Retarus Email Security
- Password-protected attachments possible
- Optional CNAME function reduces the probability that an email is classified as spam
- Calculation of opening rates with open tracking and link tracking
- FreeMarker templating support
- Easy processing of multi-recipient jobs with up to 1,000 recipients at the same time
- Integrated campaign support
- Multi-level service level agreements (SLA
s ) available - 24/7 support in multiple languages
- Support for international compliance requirements such as the EU GDPR, HIPAA, Sarbanes-Oxley, or PCI DSS, CAN-SPAM
- Continuous development
| Email delivery | REST API | SMTP |
|---|---|---|
| AntiVirus MultiScan | ||
| Campaign support | ||
| Enforced TLS | ||
| Envelope-From Address Rewriting | ||
| Guaranteed throughput | ||
| Invoicing according to account/cost center | ||
| Multi-recipient jobs | ||
| Open tracking and link tracking | ||
| Reference information | ||
| Secure Document Handling | ||
| Smart delivery optimization | ||
| Template Rendering | ||
| Trace & Recover | ||
| Unsubscribe support | ||
| User-defined X header |
CSA Certification

Retarus data centers are CSA certified. The Certified Senders Alliance (CSA) aims to increase the quality of commercial emails (for example, newsletters, invoices, and order confirmations). This is done by creating quality standards that must be technologically and legally observed.
- No spam score check for CSA-certified ISPs and technology partners; high rate of delivery to the recipient's inbox
- Higher throughput per unit of time, no or reduced throttling
- Unsubscribe options
- DKIM signature for secure authentication
- Protection against fake sender addresses via SPF
- Effective early warning system thanks to CSA mechanisms
- Emails sent in compliance with current privacy regulations
- Large international ISP network
Envelope-From Address Rewriting
The rewriting of sender addresses for outgoing emails simplifies, in many cases, the implementation of company-internal policies. For example, when company-internal domains should not be used for external communication. Therefore, Retarus offers the option of automatically rewriting your envelope from-address for outbound emails so that any replies can be rerouted directly to a dedicated inbox.
Global Availability, Local Processing, Compliance
Retarus Transactional Email is available worldwide as part of the Retarus Enterprise Cloud. Retarus can guarantee local data processing upon request. All data centers are operated according to the latest standards and fulfill strict requirements set forth by financial service providers and the health care industry.
- Failover or load-balancing options in Retarus' data centers with local, independent access in Europe, Asia, and the US
- Integration via modern API
s - Multi-client capability thanks to multi-domain configuration
- Support for international compliance requirements such as the EU GDPR, HIPAA, Sarbanes-Oxley, or PCI DSS, CAN-SPAM
Reputation Management
Outgoing emails are checked to determine the reputation of the sender. The authorization of senders is evaluated by implementing the following verification functions: SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting and Conformance). Classified emails that do not pass validation are isolated in a quarantine.
- Reputation management – SPF, DKIM and DMARC validation
- Assignment of dedicated IP addresses (recommended when sending more than 1,000,000 emails per month)
- Dynamic IP routing according to sender domain
- Support of IPv4 and IPv6
- Ability to send large emails (attachment limiter) up to 20 MB
- Filter function for critical file types (e. g. exe) and role-based recipient addresses (e. g. noreply@)
- Less blacklisting thanks to different IP addresses for transactional, marketing, and P2P emails
- Blacklist and reputation monitoring with monitoring of more than 50 international blacklisting providers
- Blocking of unknown recipient addresses (suppression list)
- Feedback loop service automatically reports if and which emails are rejected by recipients and prevents resending to recipients who have declined receipt of specific emails from the ISP
- SNDS (Smart Network Data Services) reporting supplies data that can be used to evaluate the reputation of Microsoft communication partners and optimize as needed
- Spam Score Check scans emails before they are sent to determine their spam probability, based on known factors such as formatting, hyperlinks, and so on
- Smart Delivery Optimization intelligently manages the batch sending of emails per sending domain and can therefore automatically adapt the sending behavior to the requirements of each ISP and email provider. This actively minimizes the risk of being blocked or even blocklisted.
| Reputation management | REST API | SMTP |
|---|---|---|
| Blocklist monitoring | ||
| CSA certified | ||
| Dedicated IP (optional) | ||
| Feedback loop service | Email API callback | Email API callback |
| Registered sender domain | ||
| SPF / DKIM / DMARC | ||
| Support of IPv4 and IPv6 | ||
| Suppression list (hard bounces) |
Secure Document Handling
Secure Document Handling allows you to encrypt the files you want to attach to your outgoing emails. The files are automatically added to a ZIP archive in the Retarus infrastructure and encrypted with a password. Retarus sends the passwords separately to the recipients of the corresponding emails. To ensure the best possible protection for your recipients, this service is offered together with our AntiVirus MultiScan.
Comprehensive Status Messages
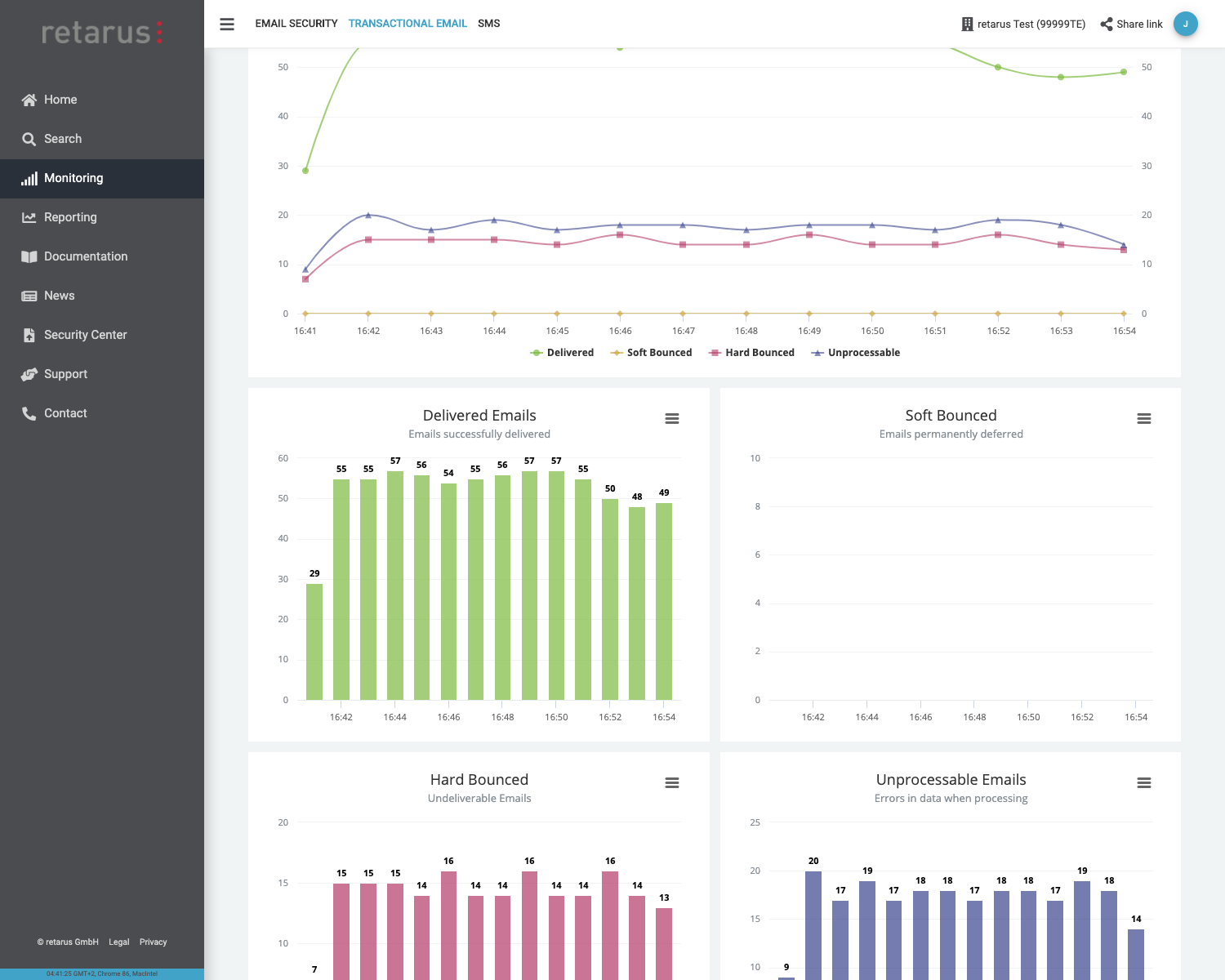
Detailed monitoring, which Retarus Transactional Email makes available in real time, can be used to check the status of a sent email at all times.
- Status information via API callback (webhook) or non-delivery report (NDR)
- Information about the delivery status, reason for undeliverability, blocked emails sent to recipients recorded in the suppression list, or open and click rates, etc.
- Detailed information about each final SMTP status, e.g. recipient MTA, time stamp, operating system, email client, etc.
- Automated integration of status information in business processes and applications
- Simple master data maintenance (list hygiene), easier bounce and traffic management, better domain reputation
- Live monitoring in the EAS Portal for tracking transmission jobs in real time
- Email Live Search makes it possible to search through transmission jobs in real time
Service Options
| Service options | REST API | SMTP |
|---|---|---|
| Authentication via sender IP | ||
| Data format | JSON | SMTP/MIME |
| Global processing | EU CH USA APAC |
EU CH USA APAC |
| IP allowlisting (API) | ||
| Multi-client capable (multi-domain configuration) |
Reporting
| Reporting | REST API | SMTP |
|---|---|---|
| Detailed delivery reporting (EAS) | ||
| Search via live search (EAS) | ||
| SNDS reporting | ||
| Status information for each email | API callback (webhooks) | API callback (webhooks) |
| Tracking via live monitoring (EAS) |
Trace and Recover
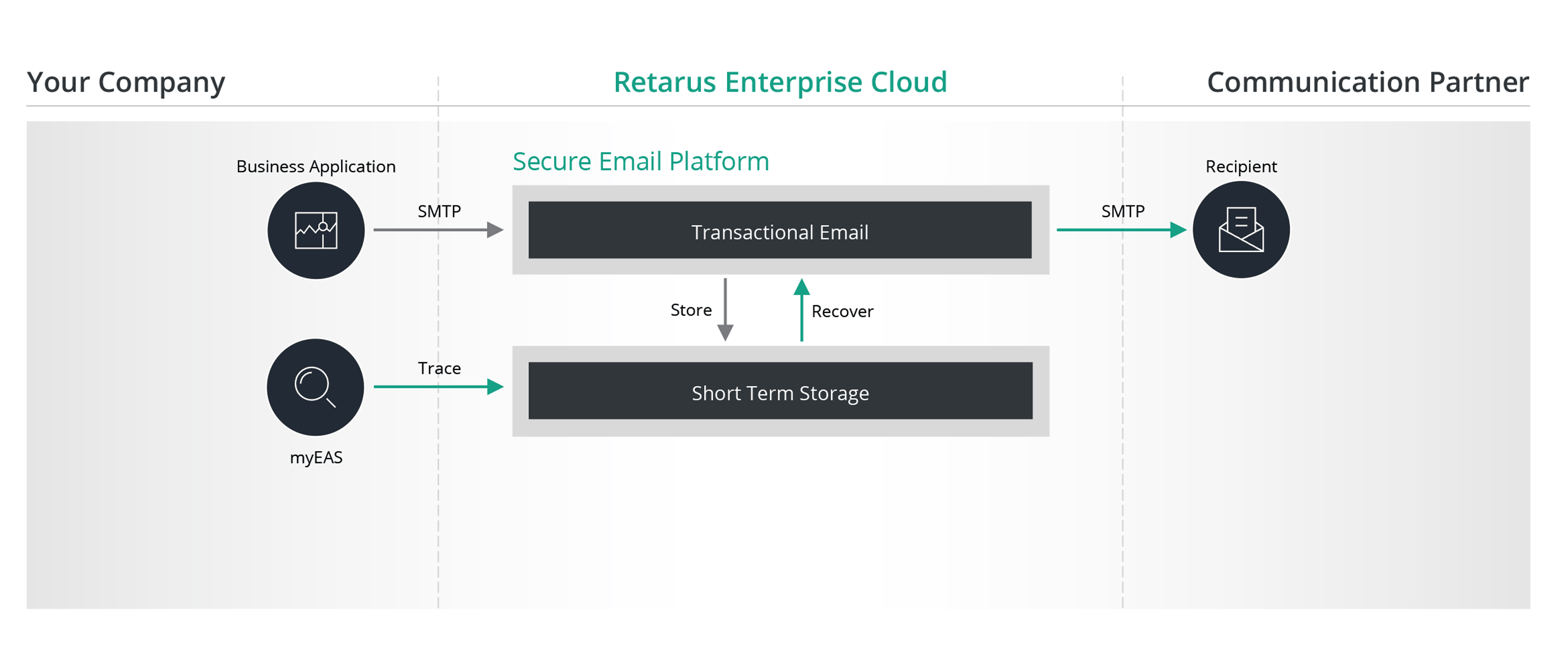
Trace and Recover
Trace and Recover safeguards your application traffic by caching transactional emails securely in an intelligent short-term storage.
- Smart temporary storage for 45 days
- Simple search and resend option for support and contact center workers
- Add reference details (e.g. customer or process numbers) for even easier search
- Preview capability for emails before resending
- Edit recipient before resending the message
- Continuous monitoring and event data for resent jobs
Bounce and Response Manager
Bounce and Response Manager
The key add-on to Transactional Email for inbound emails. The Bounce and Response Manager provides you and your employees an overview of your inbox at all times, even when email volumes are high. Keep out of office replies and hard bounces separate from legitimate customer inquiries to facilitate faster response and reply times.
- Manage, organize, and route incoming emails, especially responses to transactional emails - processed in Retarus' datacenters in Europe
- Traffic handling and workflow automation for marketing, support, and contact center
- Meets the highest performance and compliance requirements especially for complex corporate environments
- Completely cloud based; integral component of the Retarus Secure Email Platform
- Automated virus scan for all incoming emails
Email Continuity
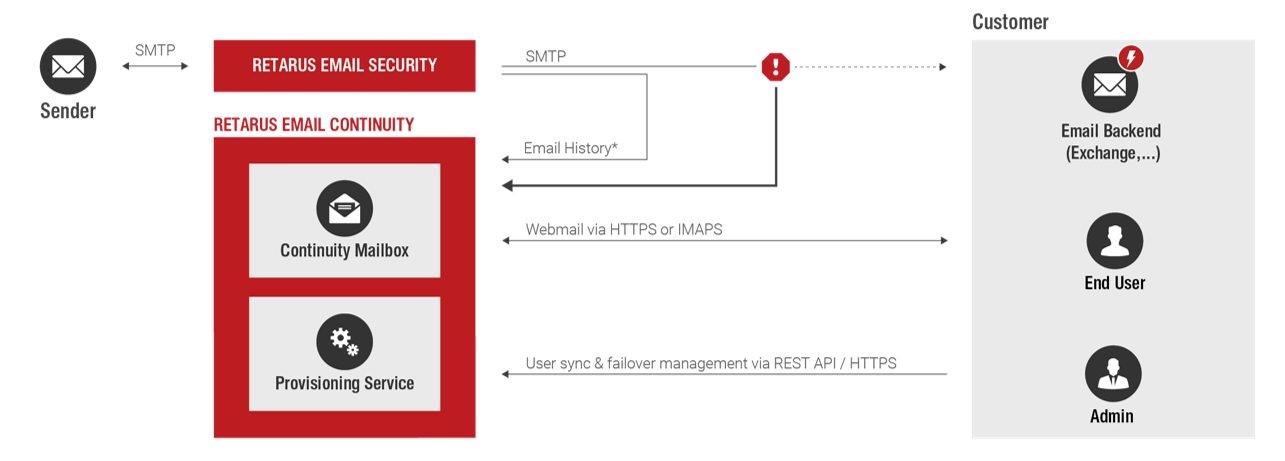
Email Continuity
- “Switch-over“ routing in case of an emergency
- End users can continue working in a common, easy-to-use webmail interface, including access to the company address book
- Optional: Email History - access to inbound emails of the past days
- Non-Microsoft environment
- Compliant: Access via protected webmailer and secure browser connection only. No export capabilities for end users or synchronization with additional or local email clients possible.
- Additional benefit: Easily provide corporate email addresses to employees not having access to internal critical email infrastructure
- Ready for immediate use:
- Automatic provisioning of webmail inboxes for end users
- Intuitive, easy-to-use interface means no training needed
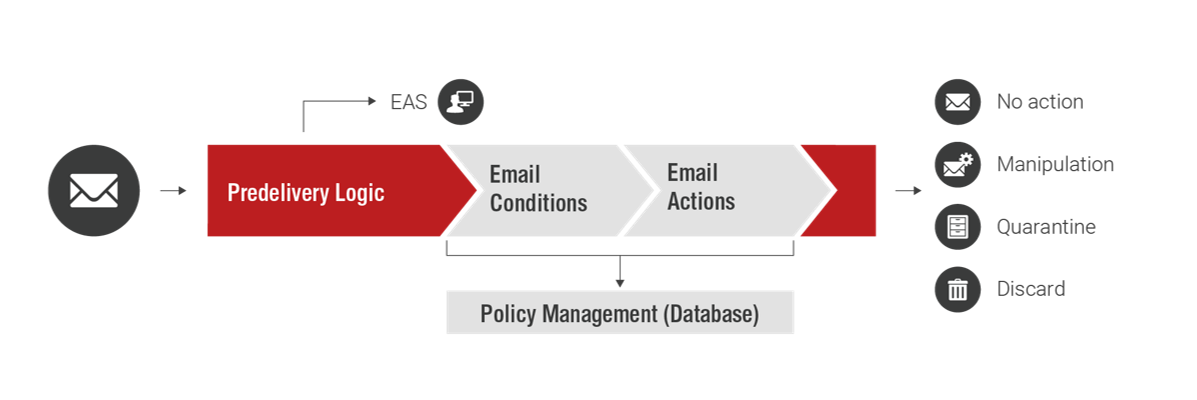
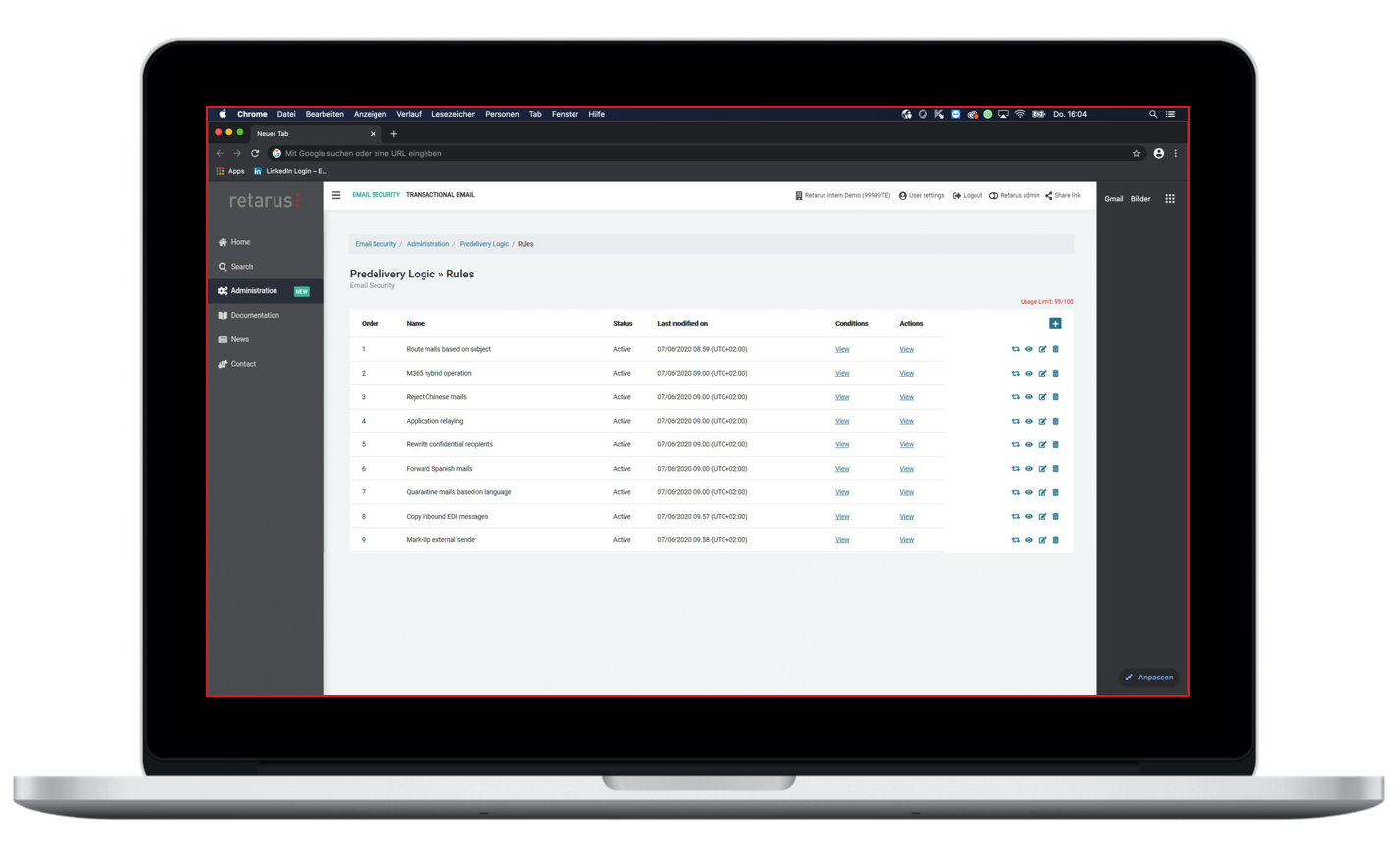
Predelivery Logic
Predelivery Logic
- Controlling, organizing and routing of all enterprise email traffic
- Facilitate specific use cases through flexibly configurable rules (consisting of predicates and actions)
- Combined solution for security, traffic handling/IT infrastructure and workflow automation
- Best performance and compliance, designed for complex enterprise environments
- Fully Cloud-based and integrated into Retarus Secure Email Platform